Documentation
Features > Break Glass / LAPS.
With the arrival of a game-changing new feature in Admin By Request version 7.3, you can eliminate the need to use Microsoft’s Local Administrator Password Solution: Break Glass Account – the more efficient, secure, and comprehensive version of Microsoft LAPS, rolled into your existing Privileged Access Management (PAM) software.
The LAPS Shortfall
The new feature is based on the idea behind Microsoft’s Local Administrator Password Solution (MS LAPS).
If you’re familiar with MS LAPS, you’ll know how it works and why it’s necessary:
- Hackers love the tried and tested technique of exploiting administrator accounts, either via horizontal or vertical privilege escalation.
- MS LAPS works to prevent this by utilizing Active Directory (AD) to manage admin account passwords across all endpoints, with a key component of management being the forced rotation of passwords for each admin account.
- When access to an admin account is needed, system admins can retrieve stored passwords from AD and log in to the administrator account.
The reasoning is valid, but MS LAPS leaves several security (and usability) gaps that we thought needing filling.
Break Glass Account – What is It?
The new Break Glass feature takes the functionality of MS LAPS and turns it into a much more attractive option:
It creates a new, temporary, one-time-use Administrator account on an endpoint, that works on domains, Azure AD, and stand-alone, which Audits all elevated activity, and terminates within a pre-defined amount of time or on log out.
The Benefits
The Break Glass Account feature incorporates the best bits of LAPS – then adds several layers of security and improves the user experience.
Security
- Break Glass completely circumvents the need to use the built-in Windows local Administrator account – you can disable it completely to add an extra later of security to your endpoints.
- The account must be used within an hour of being generated, minimizing the potential attack window and risk of account compromise.
- Risk is further minimized by a one-time-only log in functionality: the user can log in once, and after log out, the account is terminated.
- The user has only the time specified under Expiry when the Break Glass account was generated to use the administrator account; this duration is indicated on the built-in desktop background of each account. When the time-period is up, the session is terminated.
- Measures are in place to ensure the Expiry time cannot be tampered with: if the Account user attempts to extend their time limit by adjusting the clock, the Account automatically logs out / terminates.
- All Usernames and Passwords are automatically generated, random, and complex, minimizing the possibility for a successful brute force attack.
- Passwords are stored within the web application, only accessible by User Portal users / IT Admins via credentials – a safer option compared to MS LAPS’s storage of admin account passwords in plain text along with the AD computer record.
Ease of Use
With the addition of the Break Glass feature, you get a PAM solution that covers multiple bases:
- Admin rights management
- Logging capabilities
- A full inventory
- Anti-malware
- Just-In-Time provisioning
- LAPS
All combined into one security software package – eliminating the need to manage multiple security solutions on different platforms or through different applications.
Several cumbersome configuration steps required for MS LAPS setup are also eliminated with the Break Glass feature. You don’t have to deploy a Client-Side Extension (CSE) on every endpoint, extend the AD schema in order for your systems and network to accommodate the feature, configure password settings such as complexity, length, and expiry, or configure access permissions and Group Policy; we’ve already done the hard yards for you.
Possibly the best feature for ease-of-use is that the Break Glass Account does not require a domain; it works on domains, Azure AD, and stand-alone.
Real-Life Use Cases
1. Regaining Domain-Trust Relationship
As the name suggests, the Break Glass feature is ideal for ‘last resort’ situations, such as when the domain-trust relationship is broken and needs to be reconnected using an Administrator account.
2. Provisioning a Just-In-Time Administrator Account
The Break Glass Account doubles up as a Just-In-Time account that can be used for specific purposes / situations when necessary, e.g., provisioning an account for someone who doesn’t have credentials, but requires access to service an endpoint.
3. Extra Possibilities with Server Edition
Further to point 2, with Admin By Request Windows Server Edition you can provision an admin account to a consultant without giving them domain-wide permissions at any point in time.
How to Use Break Glass:
The way it works is simple, and we’ve broken it down into three stages:
Generate
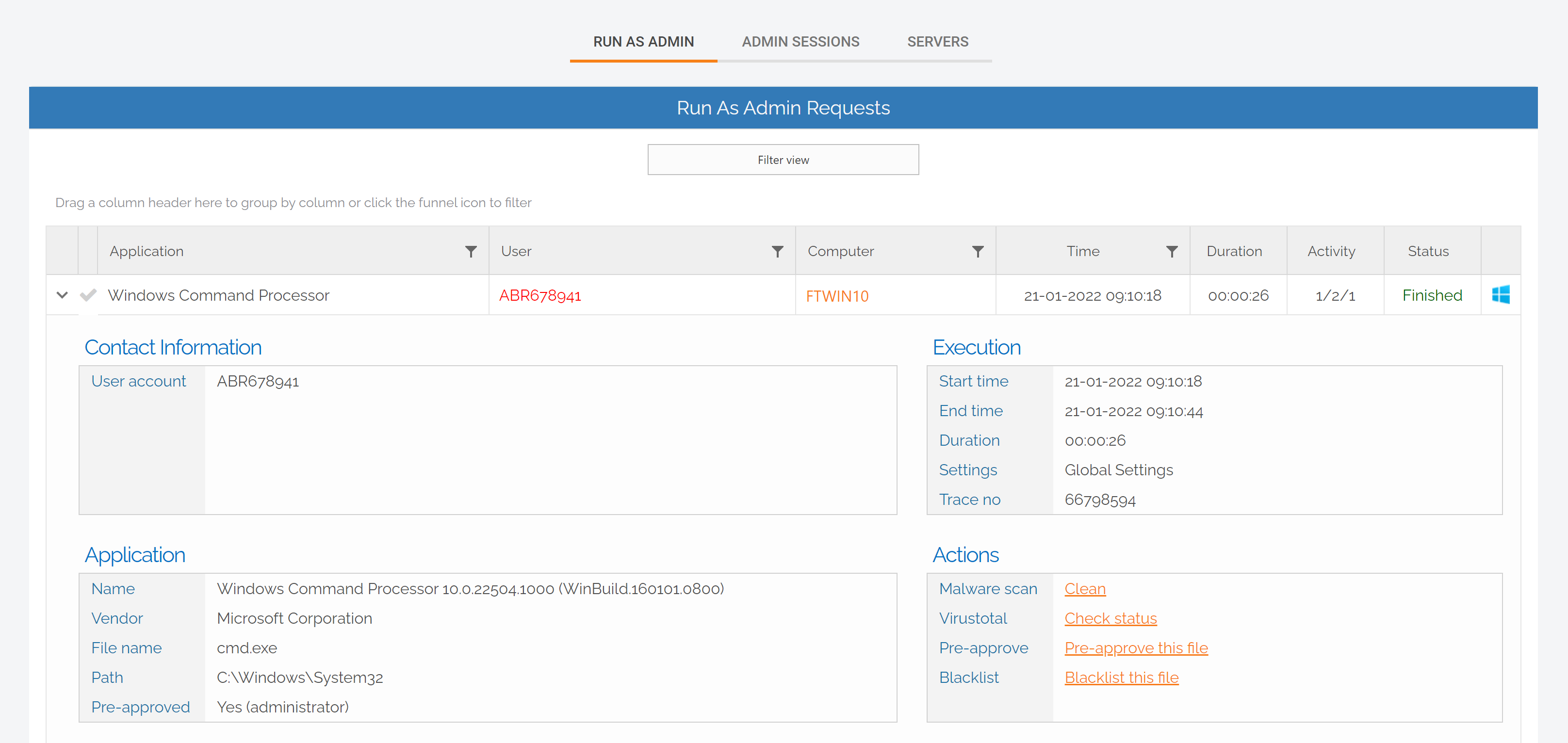
1. Log in to your User Portal and navigate to the Inventory page. Select an endpoint that you want to enable the Break Glass Account on and locate the feature listed in the left-hand menu:
.png)
2. From the Expiry drop-down menu, select an amount of time that you want the Account to be available for. This time period can range from a minimum of 15 minutes, to an unlimited amount of time:
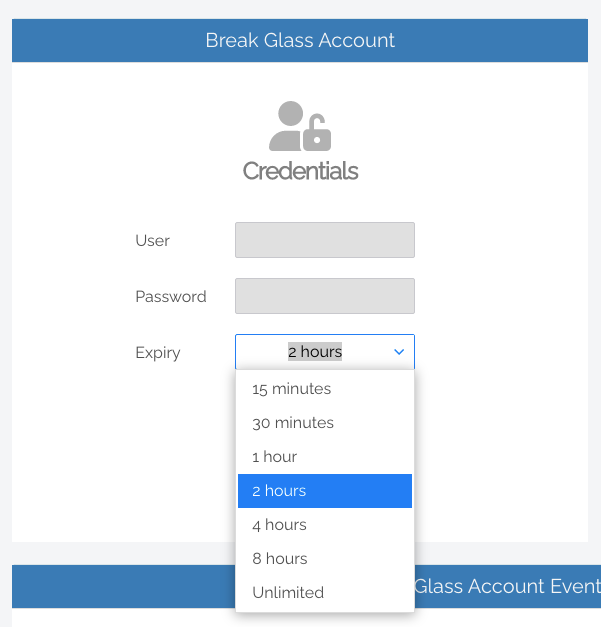
3. Click the Generate Account button, which issues a Break Glass Account and displays its Username and Password in the read-only textboxes:
.png)
4. Once generated, the status of the Break Glass Account is updated in real-time in your User Portal. The four possible states are:
- Waiting for Endpoint – The Account is generated in the User Portal but not yet created on the endpoint (to create the account on the endpoint, see the next section, Activate Account).
- Ready to Log On – The Account is created but has not yet been activated / used (i.e., logged in to).
- Session in Progress – The Account is currently in use.
- Account Removed – The Account has been terminated either due to the user logging out, or the pre-defined Expiry time being reached.
.png)
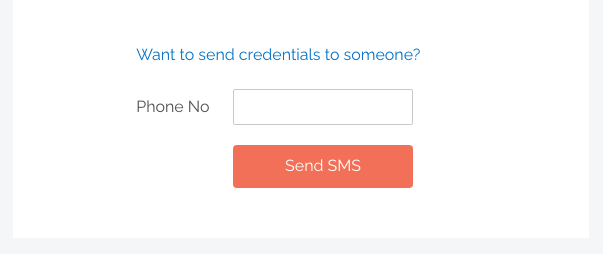
5. Optional: Send the new Break Glass Account credentials via SMS (i.e., text message) by entering the intended recipient’s mobile number into the textbox:
Activate
1. Log in / activate the Break Glass Account using one of the following methods:
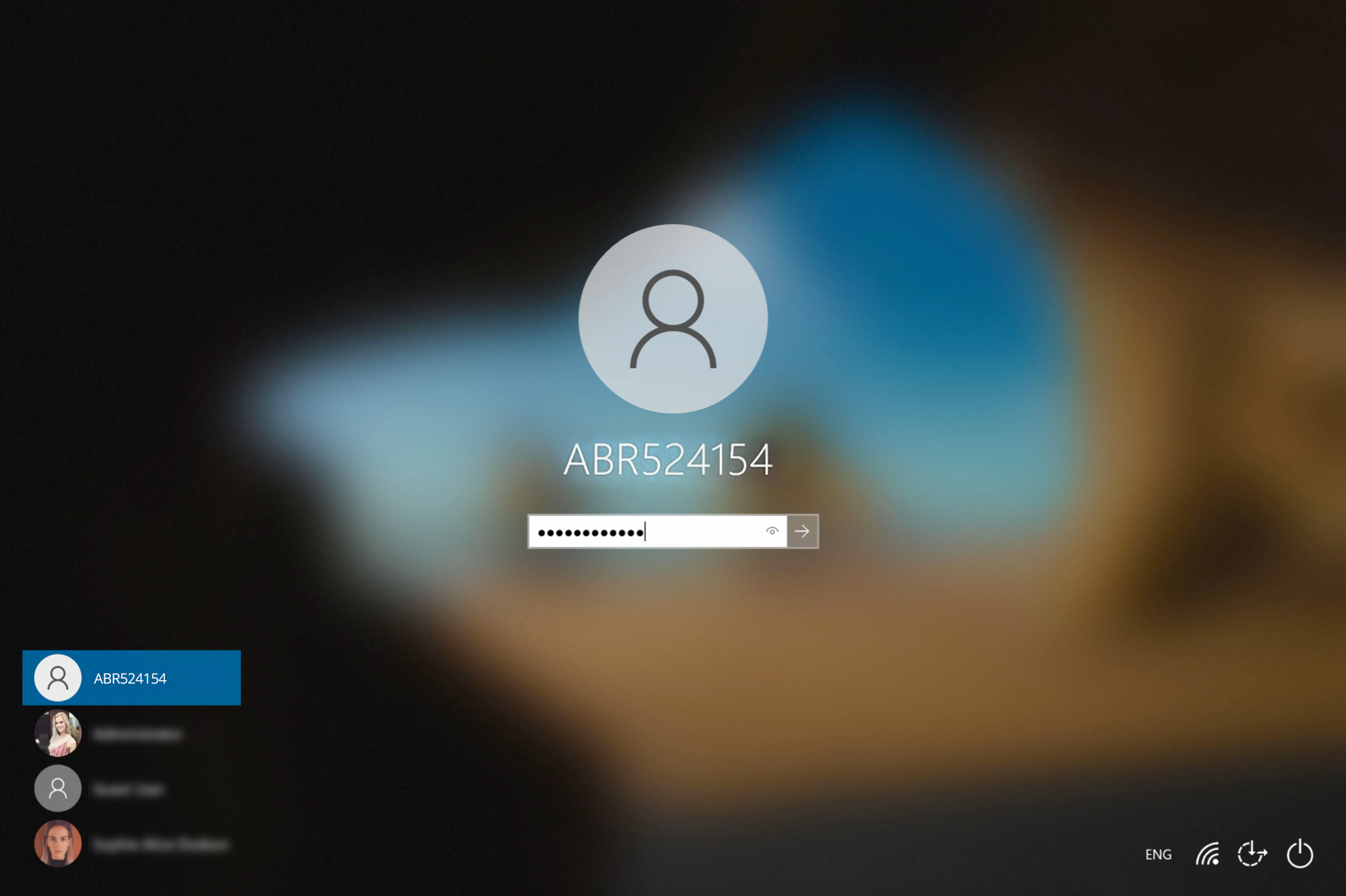
- Restart the device, then wait approximately 30 seconds for the account to be created. The User Portal will update the status message when the account is ready, and the Account will appear in the bottom-left of the Windows log on screen along with the other accounts available on that endpoint:
- If enabled, you can select Other User in the Windows log in screen and type the generated Break Glass Account Username and Password into the fields. This may fail on the first attempt; if so, wait 10 seconds and then try again.
- A third method to activate the account is by logging in to another account on the endpoint, selecting the Admin By Request icon from the bottom toolbar, and clicking the About item from the menu.
Terminate
1. Once logged in to the Break Glass account, the user has administrator privileges to do what they need to do, within the Expiry time displayed on the built-in screensaver:
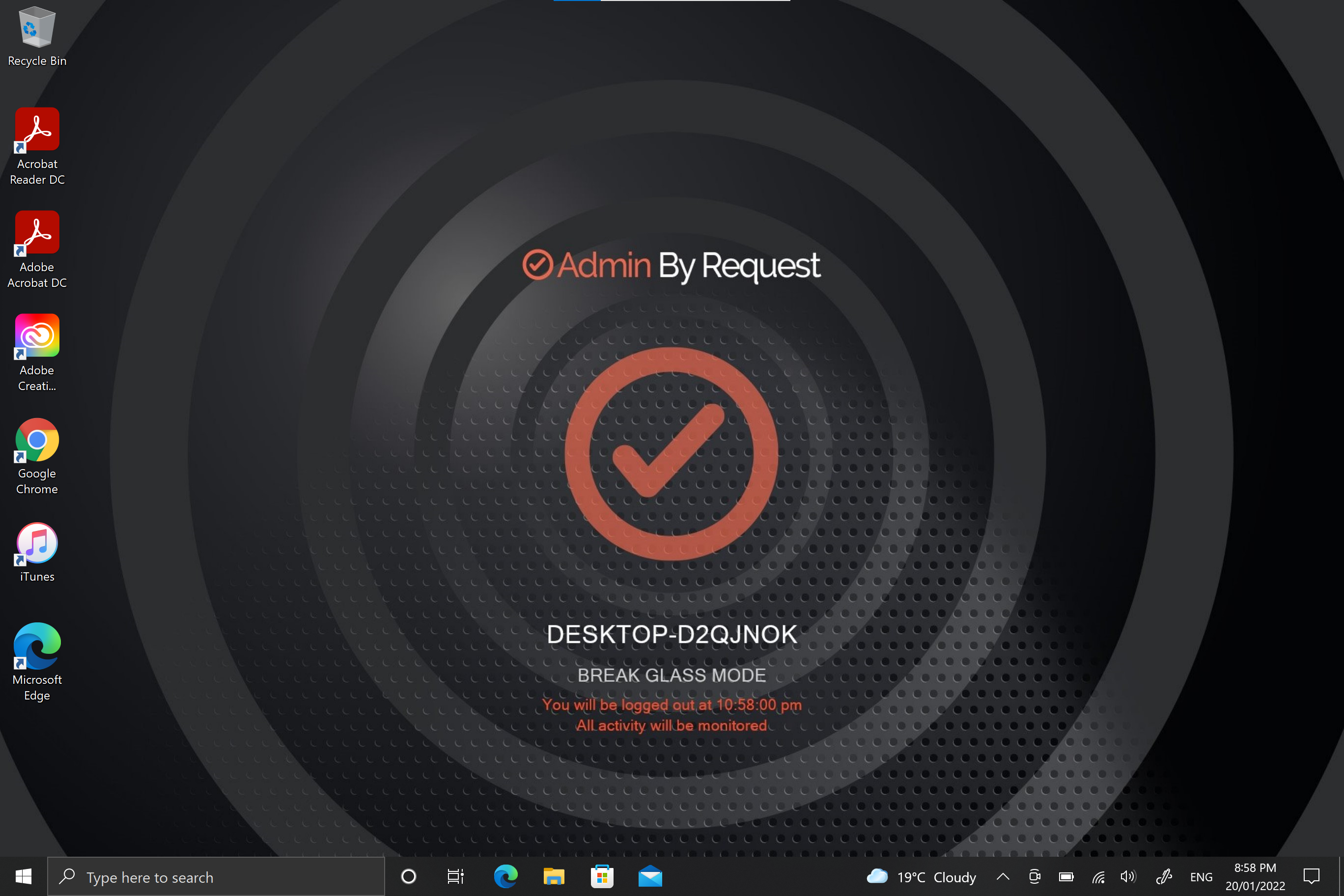
2. The account is for one-time-use only, so is terminated permanently when the user logs out, or when the Expiry time is reached – whichever comes sooner.
View Activity
1. Break Glass events such as account creation, activation, and termination are listed in the Events section of the feature page in your User Portal, color-coded, along with the time of the event and Username of the Account it belongs to:
.png)
2. Privileged activity undertaken during the Break Glass session, such as Run as Admin, is logged in the Auditlog in your User Portal:
Ditch LAPS; Break Glass
LAPS functionality is a must for adequate security, but with the Break Glass Account you get comprehensive security, ease of use, and a range of features rolled into a single PAM solution.
Download Admin By Request version 7.3 for Windows today and leave LAPS and its shortfalls behind.
LAPS / Break Glass Recording
After release, we held a webinar covering all the good stuff:
- How we got here – the need for this feature
- Generating and using a Break Glass Account – how does it work?
- Scenarios for use
- What else is new with 7.3
If you missed out, we recorded the webinar and compiled it into a shortened version covering all of the highlights. Access the recording at the button below:
Stay Up To Date
Latest Blogs
Admin By Request is Back at Gartner IAM Summit Texas This December
Admin By Request returns to the Gartner IAM Summit in Texas with live demos, a session on smarter privileged access, and authentic Texas BBQ.
Memento Labs Spyware Used in Chrome Zero-Day Campaign
Operation ForumTroll used a Chrome zero-day to install spyware traced to Memento Labs. The phishing campaign hit research and media groups.
Ransomware Recovery vs. Prevention: Why You Need Both
Ransomware attacks are inevitable. Effective cybersecurity combines prevention to stop most threats and recovery to limit damage when one succeeds.