We can all agree: ransomware perpetrators are the lowest of the low. The general consensus proved to be truer than ever during the Covid-19 pandemic when healthcare organizations – previously left alone for the most part as an ‘unspoken rule’ amongst hackers – became popular targets for cyber criminals,
Unfortunately, hackers haven’t let up in this area post-Covid. It’s been revealed by the United States Department of Health and Human Services (HHS) that one, possibly more, healthcare firms have fallen victim to ransomware over the past few months.
The culprit? Venus ransomware.
Venus Rising
Far from having the qualities of its planetary namesake (love, beauty, prosperity, victory), Venus is a run-of-the-mill piece of ransomware that targets the Windows OS.
Bleeping Computer provides the breakdown:
1. Initial access is gained via exposed RDP session – one of the two most common attack vectors, along with phishing. The hackers scan all ports (not just the default 3389 RDP listening port), listen for a response to determine an RDP connection, then likely gain access via brute force.
2. Once access to the target system is gained, the malware attempts to kill the following 39 processes relating to Microsoft Office apps and database servers:
taskkill, msftesql.exe, sqlagent.exe, sqlbrowser.exe, sqlservr.exe, sqlwriter.exe, oracle.exe, ocssd.exe, dbsnmp.exe, synctime.exe, mydesktopqos.exe, agntsvc.exe, isqlplussvc.exe, xfssvccon.exe, mydesktopservice.exe, ocautoupds.exe, agntsvc.exe, agntsvc.exe, agntsvc.exe, encsvc.exe, firefoxconfig.exe, tbirdconfig.exe, ocomm.exe, mysqld.exe, mysqld-nt.exe, mysqld-opt.exe, dbeng50.exe, sqbcoreservice.exe, excel.exe, infopath.exe, msaccess.exe, mspub.exe, onenote.exe, outlook.exe, powerpnt.exe, sqlservr.exe, thebat64.exe, thunderbird.exe, winword.exe, wordpad.exe
3. It then goes about deleting event logs, VSS Shadow Copies, and disables Data Execution Prevention using the command below:
wbadmin delete catalog -quiet && vssadmin.exe delete shadows /all /quiet && bcdedit.exe /set {current} nx AlwaysOff && wmic SHADOWCOPY DELETE
4. After all of the above is successfully completed, the stage is set for encryption. Venus appends .venus to encrypted files (in addition to the existing file extension), and a bright orange HTA ransom note is automatically displayed on the victim’s screen:
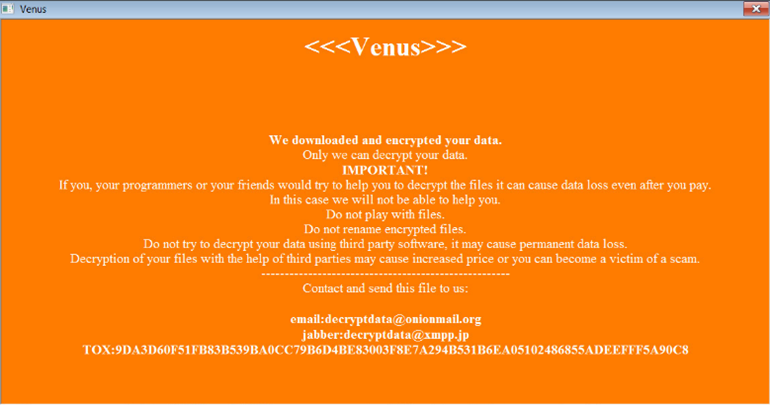
Source: Bleeping Computer
Notably, to date the perpetrators do not seem to be focused on Data leakage, instead pouring all their efforts into encryption.
Venus also doesn’t discriminate based on target type or size. As well as healthcare giants, there have been reports from individuals on Bleeping Computer who have found files on their home PCs and servers sporting the .venus extension.
Tips for Prevention
When you break it down, there are essentially three stages to the Venus attack. The first is the initial infection – the malicious software finding its way into your IT system. Then comes ‘setting the scene’ for encryption, and the third and final stage is the encryption itself. Everything prior to stage three can be recovered from if detected, but once your files are appended with the dreaded .venus… start saving for at least 1 BTC if you’re an individual, and likely upwards of 20 if you’re an enterprise. (Just kidding, it’s advised to never pay a ransom.)
Let’s start with the initial-infection attack vector, Remote Desktop Protocol (RDP). It’s a readily available direct path to another endpoint or network, and it provides native access to the victim’s system. The credentials used to create an RDP connection are usually administrator credentials, meaning if an attacker manages to obtain these, they then have full privileges on the endpoint and can do a lot more damage.
Tip 1: Stop using RDP.
In fact, with Venus (and most ransomware), elevated privileges are a requirement for stage 2: successfully preparing for encryption. Venus has to stop services and processes, delete event logs and shadow volume copies, and disable critical software prior to encryption – none of these tasks can be completed by a standard user.
Tip 2: Restrict administrative privileges.
While Venus ransomware is busy killing Windows services and deleting logs, the user remains blissfully unaware of what is happening because the exact tools that should alert them to the situation have been circumvented by the ransomware – it can proceed to the third and final encryption stage unhindered.
Tip 3: Use a third-party Auditing tool.
Turning Tips into Tools
It’s all well and good to know what you need to be doing to protect your enterprise from threats such as Venus ransomware, but putting reliable protective measures in place is a whole other ball game.
With Admin By Request Privileged Access Management (PAM) solution, each of the three stages of a Venus attack can be prevented or detected prior to successful encryption.
From the User Portal, you can block any application from running on every endpoint that the software is deployed to. Create a blanket rule that RDP can’t be used at your organization, and enforce it by Blocking the application:
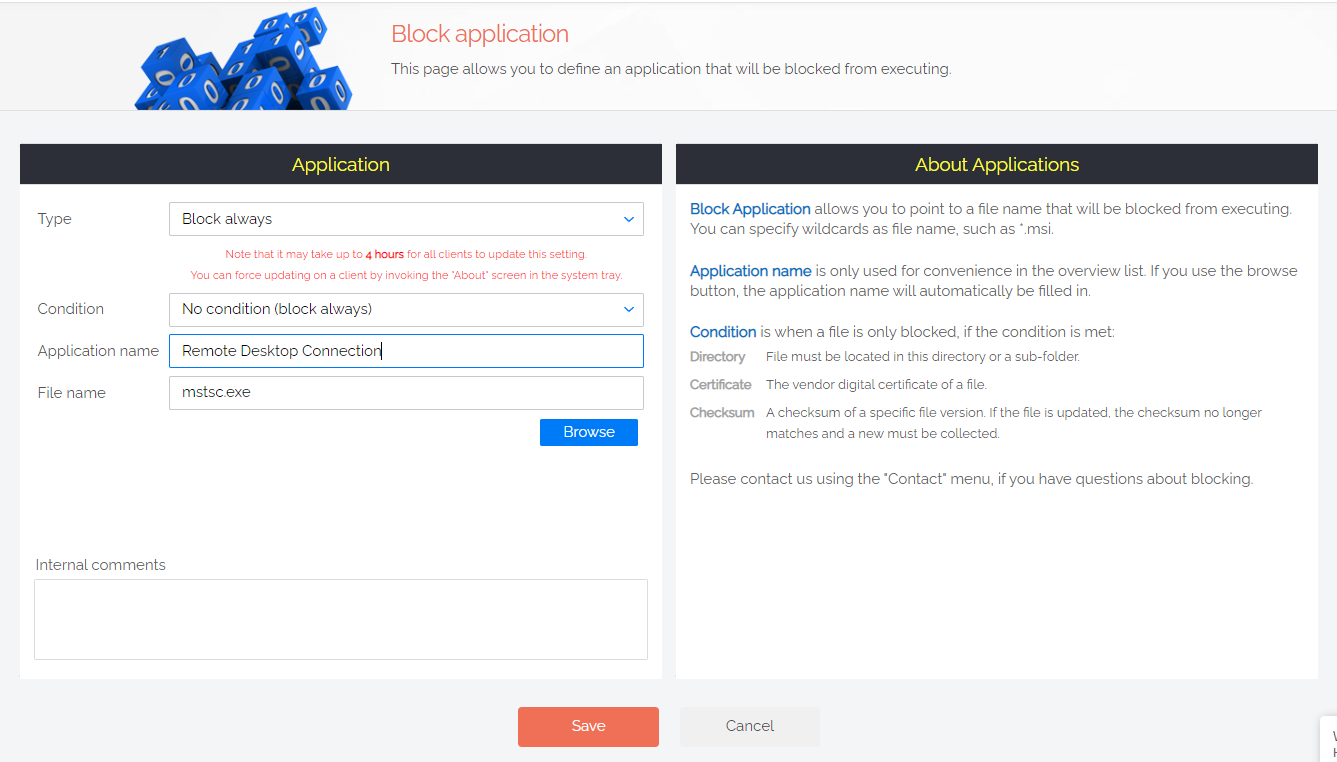
In terms of privileged access, Admin By Request allows for the instant revocation of your users’ elevated privileges. All users become standard user – unless specified otherwise in the User Portal, where you can create granular access rules for different users, groups, and OUs.
Users who require elevated privileges to do their jobs can remain productive (and protected) with Admin By request, which provides Just-In-Time elevation for individual applications upon request, rather than elevating the user or allowing them to have around-the-clock privileges.
In terms of event logging, Venus is programmed to shut down the built-in Windows tools that would give you an idea of its presence in the system. Admin By Request offers a detailed Auditlog which tracks and records all elevated activity. Actions like stopping processes, deleting privileged data, and disabling key pieces of software are all logged with relevant details such as the time, file, and the user who enacted the change included. Alerting capabilities detect actions deemed suspicious, and send desktop or email notifications based on your configuration.
TL, DR
With Admin By Request deployed and configured appropriately, Venus ransomware would be unable to enact its attack plan on your endpoints and encrypt your organization’s data.
Download the Admin By Request Free Plan or book a demo today to get started – and rest assured your enterprise won’t be the next to make headlines.






