You invest some serious money into keeping your IT environment safe from malware. Firewalls, mail scanning tools, web scanning software, proxy servers, endpoint anti-malware – you even stay up to date with patches and run the latest and greatest operating system.
But malware still worms its way in.
There is a light at the end of the tunnel (or funnel, in this case), but it doesn’t involve buying into yet another endpoint anti-malware solution that claims it will keep you 100% safe.
It won’t.
The Malware Protection Funnel
Malware can weasel its way into a computer network via several entry points, such as the internet, external storage devices and through email.
The malware protection funnel is the system of security measures in place from the network down to the end user:

- Firewalls establish a barrier between the external network, typically the internet, and your internal business network
- Web and mail traffic scanning tools do exactly that: scan your users’ incoming and outgoing HTTP and email traffic
- Endpoint anti-virus software helps prevent malware on your users’ devices using a variety of scanning and detection techniques
As for Admin By Request… we’ll get to that further on.
All of these security tools help to decrease the percentage of malware that manages to infiltrate your IT environment, and with each layer, the opening for infiltration narrows.
However, there is still an opening – the biggest vulnerability of them all:
Local administrator rights.
One Small Gap in your Network Security, One Giant Doorway for Attackers
This single vulnerability can be catastrophic for your company.
Many hackers today have financial motivation and create complex ransomware programs that often begin the process of infiltrating the system by targeting the end user.
From here, malware can vertically escalate to a more privileged position from which point it can access the core of the operating system (as is the case with RobbinHood ransomware) or horizontally propagate across the network by stealing user credentials of the same privilege level.
Both situations spell huge data breaches and subsequent disaster – and are much more common that you may realise.
In late March this year hackers gained access to hotel giant, Marriot, by obtaining the login details of two employees of the franchise. 5.2 million people were affected by the data breach which stole names, addresses, and contact information – all a result of hackers gaining access to just two user accounts.
Mid-last year the US Defence Information Systems Agency (DISA), which employs over 8000 military and civilian staff, suffered a data breach that wasn’t discovered until February 11th of this year – almost a year after the hackers gained initial access. The breach compromised employee’s PII (Personal Identifiable Information) and social security numbers, but the exact details of the breach, and those affected, have not been disclosed.
Admin By Request: The Funnel of Love (well, of safety at least)
With Admin By Request, nothing needs to be disclosed when it comes to unauthorised activity – because this software prevents unauthorised activity from occurring in the first place.
Somewhere between 80 and 100% of vulnerabilities can be eliminated by eliminating local administrator rights. But that’s not always practical: your users need admin rights to be able to do simple day to day tasks, such as installing media players or PDF readers.
So how do you find a happy medium between keeping your system safe and keeping productivity at a maximum?
By simply managing privileged access.
Funnel your Users: Managing User Access
Admin By Request is A Privileged Access Management (PAM) solution. It deals with the open doorway that is your user endpoints, allowing you to revoke admin rights so that malware has a much harder job of gaining entry to your IT system.
With Admin By Request, you can choose who gets what access.
The software’s sub settings allow you to create different access rules for organizational groups. You can set tight access restrictions for some users and allow more leniency for others who might need higher privileges on a more regular basis, such as the IT team.
Admin By Request keeps you safe by reducing the number of potentially vulnerable privileged users – but what about productivity? What do your limited-access users do when they need to run programs and processes that require administrator credentials?
Funnelling out: How it Works
Admin By Request provides four ways for users to do such tasks without elevating them to full-time privileged users.
These methods include:
- Whitelisting commonly used applications ahead of time
- Allowing users to request elevation of an app, which can then be run with administrator privileges
- Allowing users to request a timed elevated session, which gives them administrative access to their system for the duration of the session
- Providing a one-time-use PIN to a user (who may fall outside the scope that allows them to use either of the previous two self-initiated methods). The PIN allows them to gain elevated access for a period of time.
Read more about these elevation methods here.
These techniques prioritise security by:
o Whitelisting and elevating apps rather than giving the user local administrator rights and
o Applying the concept of Just-in-time (JIT) elevation – only elevating privileges when and where they are absolutely necessary.
Just like that, Admin By Request balances security and productivity.
.png)
Shedding Some Light: Stay in the Know
As well as managing who gets access to what, Admin By Request‘s auditlog allows you to stay on top of what’s going on when users request administrator access.
When a user requests to run an application as administrator or begins an elevated session, the processes that occur during this period are recorded in the Admin By Request auditlog. This means installs and uninstalls are visible, and any attempt at privilege escalation is immediately detectable and can be addressed accordingly.
You won’t have to worry about discovering a data breach that happened almost a year ago with Admin By Request’s auditlog tracking every administrator-move – with requests for admin elevation and the auditlog being accessible from your phone via the Admin By Request app.
Funnel Vision: When ‘100% Safe’ Isn’t Really That Safe
Admin By Request tackles the end-user vulnerability, and with it, 80 to 100% of vulnerabilities within your network. But what about that other potential 20%?
This is where the anti-malware portion of the malware protection funnels comes back into play.
Single end-point anti-virus solutions often claim to be 100% successful at detecting malware. But with the ever-growing and mutating malware threats appearing every year, no anti-malware engine can realistically claim 100% safety and security.
Admin By Request recognises that eliminating 80 to 100% of vulnerabilities isn’t guaranteeing you 100% security – so they have integrated with Opswat’s MetaDefender Cloud to get you as close to 100% as possible.
Opswat’s Detection Efficacy overview gives an honest reflection of just how safe you are using four, through to more than twenty, anti-virus engines:
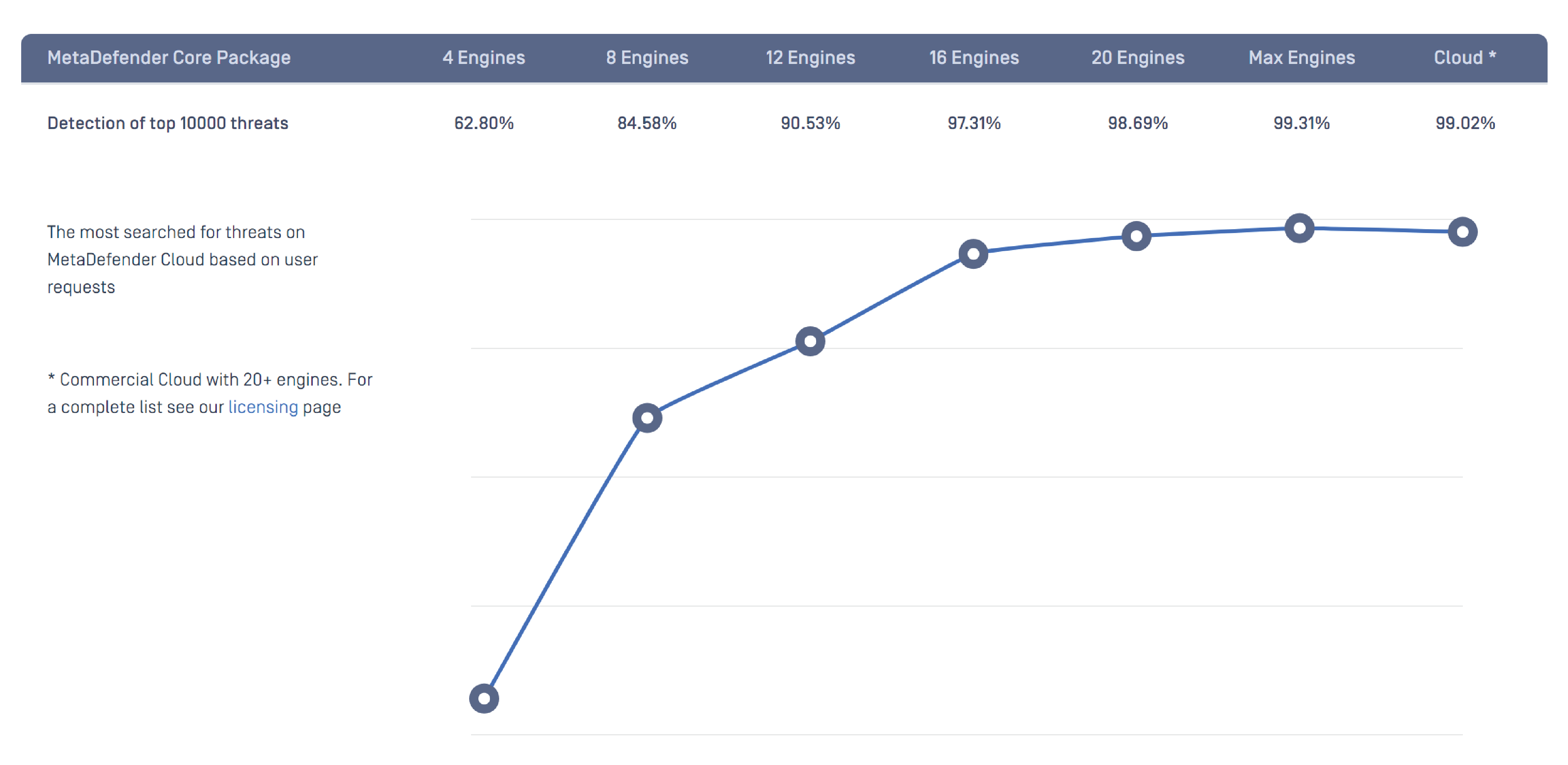
With Admin By Request’s partnership with Opswat, your files are multiscanned with over 30 anti-malware engines. The detection rate is much higher than using just one anti-virus solution.
Funnel Out
The next time you suffer a data breach and consider investing in the latest next-gen firewall and a ‘100% successful’ end-point anti-virus solution… stop.
Target the real vulnerability: local administrator rights.
And with Admin By Request, you really will get pretty darn close to 100% security.







