There seems to be a snake in the grass causing disruptions at two well-known industrial enterprises, Japanese automobile manufacturer, Honda, and Energy Company, Enel Argentina.
Here’s what’s been reported so far:
- The two companies were hit by cyber attacks that were both discovered in the late hours of Sunday June 7th.
- The New York Times reports that the following morning, Monday June 8th, employees at Honda were unable to open files and emails, with company representative Misako Saka stating the malware had “penetrated an internal server and then spread.”
- A spokesperson said the organisation suffered a loss in connectivity: experiencing difficulties in accessing email, servers and internal systems. The disruption threw a wrench in the works of business operations and production, with Honda’s computer networks across the globe being affected.
- Enel Group also confirmed in a statement to BleepingComputer that there was a disruption on its internal IT network, which it then temporarily isolated to “carry out all interventions aimed at eliminating any residual risk.”
A New Breed of Serpent
The cyber attack is believed to be ransomware: a particularly nasty type of malware that aims to steal or encrypt data and threatens to expose it or continue to block access to it unless a ransom is paid.
The attack has been tied to the Snake ransomware family – also known as ‘EKANS’ (snake backwards) – which first reared its head in early 2020.
There are several reasons for the belief that Snake is behind the attack:
- Honda and Enel Group are both large, industrial enterprises.
Snake ransomware is known for targeting large, Industrial Control System (ICS) environments, typically used in factories for automating processes. Snake ransomware can lock, shut down or even delete these ICS processes (effectively halting production for the victim company). It then encrypts data and demands a ransom for decryption. The reason ransomware like Snake targets larger organisations is to extort a greater ransom which is more likely to be paid; under mounting pressure from loss of production, the victim company must weigh up the cost of paying the ransom in the hope of recovering faster vs. withholding the ransom and losing out over extended downtime and a longer recovery period.
- The attack happened on a weekend.
Snake ransomware is a hand-launched attack, as opposed to an automated one. The attacks on both Honda and Enel were first noticed on a Sunday; most human-controlled attacks are launched on weekends as their operators know there are likely to be fewer security personal on-hand during this time.
- It targeted entire networks.
Honda suffered compromised connectivity and affected networks in Japan, the US and Europe. Enel also found its corporate network disrupted as a result of the attack. Human-operated attacks such as Snake ransomware often target an organisation and infiltrate the entire network by slowly gaining privileged access. This ensures maximum destruction when they launch the main part of the attack (in the case of Snake ransomware: encryption) and enables attackers to infect multiple devices across the network rather than impacting just one device.
- The attack was targeted.
Based on samples of the malware posted online, the ransomware appears to have been coded to target Honda and Enel’s networks specifically:
1. It checks for the internal network name of mds.honda.com and enelint.global before executing.
– When BleepingComputer attempted to analyse the sample of Snake ransomware submitted to VirusTotal, the ransomware would begin and then exit immediately without doing any encryption. This is because the ransomware attempts to resolve to the mds.honda.com or enelint.global domains but terminates when it fails to do so. It was essentially coded to only encrypt files if it was on the targeted network – in this case: Honda and Enel.
2. It refers to IP addresses that resolve to the targets’ hostnames.
– As well as checking for the mds.honda.com network name, the Snake sample contains a reference to US IP address 170.108.71.15, which resolves to hostname unspec170108.amerhonda.com. A similar check exists against an internal Enel IP address to confirm the malware is running on its target network.
All of these points are strong indicators of Snake ransomware being the culprit behind both companies’ technical issues.
How Does Snake Ransomware Slither In?
Written in GoLang (short for Go Language, but also known simply as Go), Snake is an aggressive strain of ransomware that uses a high level of obfuscation in its code, making it much more difficult to analyse.
There is a belief that Snake and other forms of ransomware are written in GoLang because the code can be compiled by all three major operating systems: Windows, macOS and Linux. This means developers can write a single ransomware application that can target victims across multiple platforms.
According to an analysis done by Acronis, Snake ransomware infections run through the following processes:
1. Snake is distributed via malicious email attachments, spam, ads, fake updates and infected installers, among others. Its point of entry is often through an insecure Remote Desktop Protocol (RDP) configuration.
– An RDP is a Microsoft protocol which allows the user to remotely connect to another computer over a network connection using a graphical interface.
2. Once executed, Snake removes the computers Shadow Volume Copies to eliminate Windows backups.
– Shadow Volume Copies are snapshots or backup copies of computer files or volumes.
3. The ransomware runs through a hard-coded list of processes to kill. These processes include virtual machines, Supervisory Control And Data Acquisition (SCADA) control systems, network management software and ICS processes, mentioned earlier. Acronis’ analysis of the virus identifies the following processes force-stopped by Snake, along with their description:
| Process | Description |
| bluestripecollector.exe | BlueStripe Data Collector |
| ccflic0.exe | Proficy Licensing |
| ccflic4.exe | Proficy Licensing |
| cdm.exe | Nimsoft Related |
| certificateprovider.exe | Ambiguous |
| client.exe | Ambiguous |
| client64.exe | Ambiguous |
| collwrap.exe | BlueStripe Data Collector |
| config_api_service.exe | ThingWorx Industrial Connectivity Suite, Ambiguous |
| dsmcsvc.exe | Tivoli Storage Manager Client |
| epmd.exe | RabbitMQ Server (SolarWinds) |
| erlsrv.exe | Erlang |
| fnplicensingservice.exe | FLEXNet Licensing Service |
| hasplmv.exe | Sentinel Hasp License Manager |
| hdb.exe | Honeywell HMIWeb |
| healthservice.exe | Microsoft SCCM |
| ilicensesvc.exe | GE Fanuc Licensing |
| inet_gethost.exe | Erlang |
| keysvc.exe | Ambiguous |
| managementagenthost.exe | VMWare CAF Management Agent Service |
| monitoringhost.exe | Microsoft SCCM |
| msdtssrvr.exe | Microsoft SQL Server Integration Service |
| msmdsrv.exe | Microsoft SQL Server Analysis Services |
| musnotificationux.exe | Microsoft Update Notification Service |
| n.exe | Ambiguous |
| nimbus.exe | Broadcom Nimbus |
| npmdagent.exe | Microsoft OMS Agent |
| ntevl.exe | Nimsoft Monitor |
| ntservices.exe | Ambiguous |
| pralarmmgr.exe | Proficy Related |
| prcalculationmgr.exe | Proficy Historian Data Calculation Service |
| prconfigmgr.exe | Proficy Related |
| prdatabasemgr.exe | Proficy Related |
| premailengine.exe | Proficy Related |
| preventmgr.exe | Proficy Related |
| prftpengine.exe | Proficy Related |
| prgateway.exe | Proficy Secure Gateway |
| prlicensemgr.exe | Proficy License Server Manager |
| proficy administrator.exe | Proficy Related |
| proficyclient.exe | Proficy Related |
| proficypublisherservice.exe | Proficy Related |
| proficyserver.exe | Proficy Server |
| proficysts.exe | Proficy Related |
| prprintserver.exe | Proficy Related |
| prproficymgr.exe | Proficy Plant Applications |
| prrds.exe | Proficy Remote Data Service |
| prreader.exe | Proficy Historian Data Calculation Service |
| prrouter.exe | Proficy Related |
| prschedulemgr.exe | Proficy Related |
| prstubber.exe | Proficy Related |
| prsummarymgr.exe | Proficy Related |
| prwriter.exe | Proficy Historian Data Calculation Service |
| reportingservicesservice.exe | Microsoft SQL Server Reporting Service |
| server_eventlog.exe | Proficy Event Log Service, Ambiguous |
| server_runtime.exe | Proficy Related, Ambiguous |
| spooler.exe | Ambiguous |
| sqlservr.exe | Microsoft SQL Server |
| taskhostw.exe | Windows OS |
| vgauthservice.exe | VMWare Guest Authentication Service |
| vmacthlp.exe | VMWare Activation Helper |
| vmtoolsd.exe | VMWare Tools Service |
| win32sysinfo.exe | RabbitMQ |
| winvnc4.exe | WinVNC Client |
| workflowresttest.exe | Ambiguous |
4. Snake ransomware checks that it doesn’t already exist on the system, searching for mutex value EKANS. If this mutex exists on the system, the ransomware will stop and show a message indicating the device is already encrypted. If not, the mutex value is set.
– A mutex (short for mutual exclusion) is a synchronizer used to ensure that in a multi-threaded application (an app that has multiple threads executing in a shared address space) only one thread can access the shared resource at a time.
5. Encryption proceeds, with Windows Management Instrumentation (WMI) calls executing today’s standard ransomware function of mixing symmetric and asymmetric cryptography algorithms.
– WMI is essentially a database of specifications on the Windows operating system: a centralised place for the management of applications and devices in a network.
– WMI allows for the remote and local management of Microsoft computers: programming processes, obtaining lists of installed applications and accessing information on classes and instances, among other functions.
6. With the encryption of each file, Snake ransomware appends a random five-character string to the original file extension. For example, a Python PYD file _multiprocessing.pyd could read _multiprocessing.pydHsTYlafter encryption. Within each file, Snake ransomware appends the file marker .EKANS. The adding of a random string adds to the obfuscation of the of the malware and sets Snake apart from most ransomware, which usually adds a discernible string to encrypted files.
7. When encryption is complete, Snake drops the following text doc to the victim:
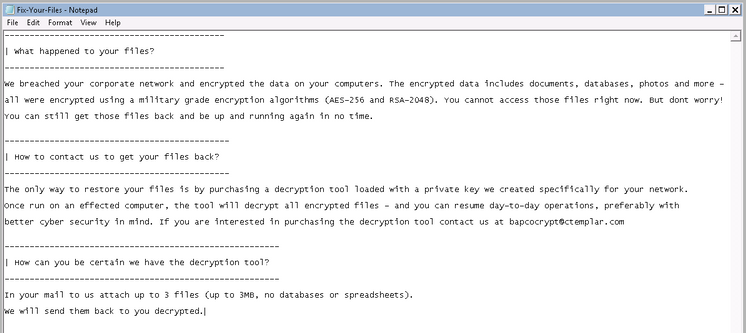
Throughout the infiltration and attack, Snake ransomware does not shutdown or restart the computer, and it allows user access throughout the encryption process.
Stopping the Snake in its Tracks
So how do industrial companies prevent unwanted serpents from stealing into the network?
By disrupting Snake ransomware’s infiltration of the system: a task it must undertake in order to launch the encryption attack.
To inflict maximum damage, Snake ransomware needs to gain administrative access.
Admin access enables the ransomware to:
- Propagate across the network
– Snake needs this to target the entire company rather than individual users
- Access system files
- Access the Windows registry
- Stop services
– Such as ICS processes
- Write to the Public directory
– (C:\Users\Public) where it is able to display the ransom note Fix-Your-Files.txt as the background of every user in the system. If it does not have administrator access, it cannot access the Public directory and the ransom note will be placed in \Users\[yourname]\AppData\Local\VirtualStore where users are likely to miss it.
o This point alone is a dead giveaway that Snake assumes it will gain administrator access and everyone in the system will forcibly be made aware of the compromise upon launch.
o Another indicator that Snake is confident in full network infiltration is the following sentence in the ransom note: “The only way to restore your files is by purchasing a decryption tool loaded with a private key we created specifically for your network”. There is no mention of decrypting files on individual computers; Snake is solely interested in the network as a whole.
To stop the Snake in its tracks, you essentially need to prevent it from gaining administrative access.
Admin By Request: Snake Charmer of the Network
Privileged Access Management (PAM) is the solution that allows you to do this.
Admin By Request is one such solution.
It’s easy to deploy, manage and maintain, revoking admin rights with minimal disruption to your users. They can continue as they always have, using one of the four methods provided to do the things they need to do unhindered – the difference is, your network is now protected from malware that aims to gain administrative access, like Snake ransomware.
Admin By Request allows you to keep a close eye on users and admins. The auditlog displays recent administrator activity. From here you can detect any activity that could indicate infiltration to your network or privilege escalation.
The user portal enables you to manage different users, with sub-settings allowing for different settings to be configured for individual users or groups of users.
Admin By Request’s PAM solution comes with an IOS and Android-supported app, meaning you can keep administrative access in check at all times, from any location – even while away from the office on weekends, when hand-launched attacks like Snake ransomware are more likely to hit.
Admin By Request ensures a malware detection rate of 99.02% thanks to integration with Opswat’s MetaDefender Cloud: an anti-malware solution that scans files with over 30 anti-malware engines.
Need to Sssssseee it to Believe It?
Admin By Request allows you to create an Admin By Request simulation file – an XML file with the .abrsim extension – using a checksum that you want to simulate a real-world situation for.
When you double click on the .abrsim file that you’ve created, Admin By Request will process the file as if it were the real file with this checksum, but will not execute anything.
This essentially allows you to simulate a malware situation without using a malicious file.
We ran a malware simulation using an Admin By Request simulation file, Snake.abrsim; the real-world scenario of this would be to have the actual file and run it as administrator.
Here’s a breakdown of this simulation on a system with Admin By Request installed:
1. Admin By Request blocks the file and displays the following window:
.png)
2. The auditlog in the Admin By Request user portal displays key information about the file, including the details of the user who tried to run it, and that the malware scan came back as Malicious:
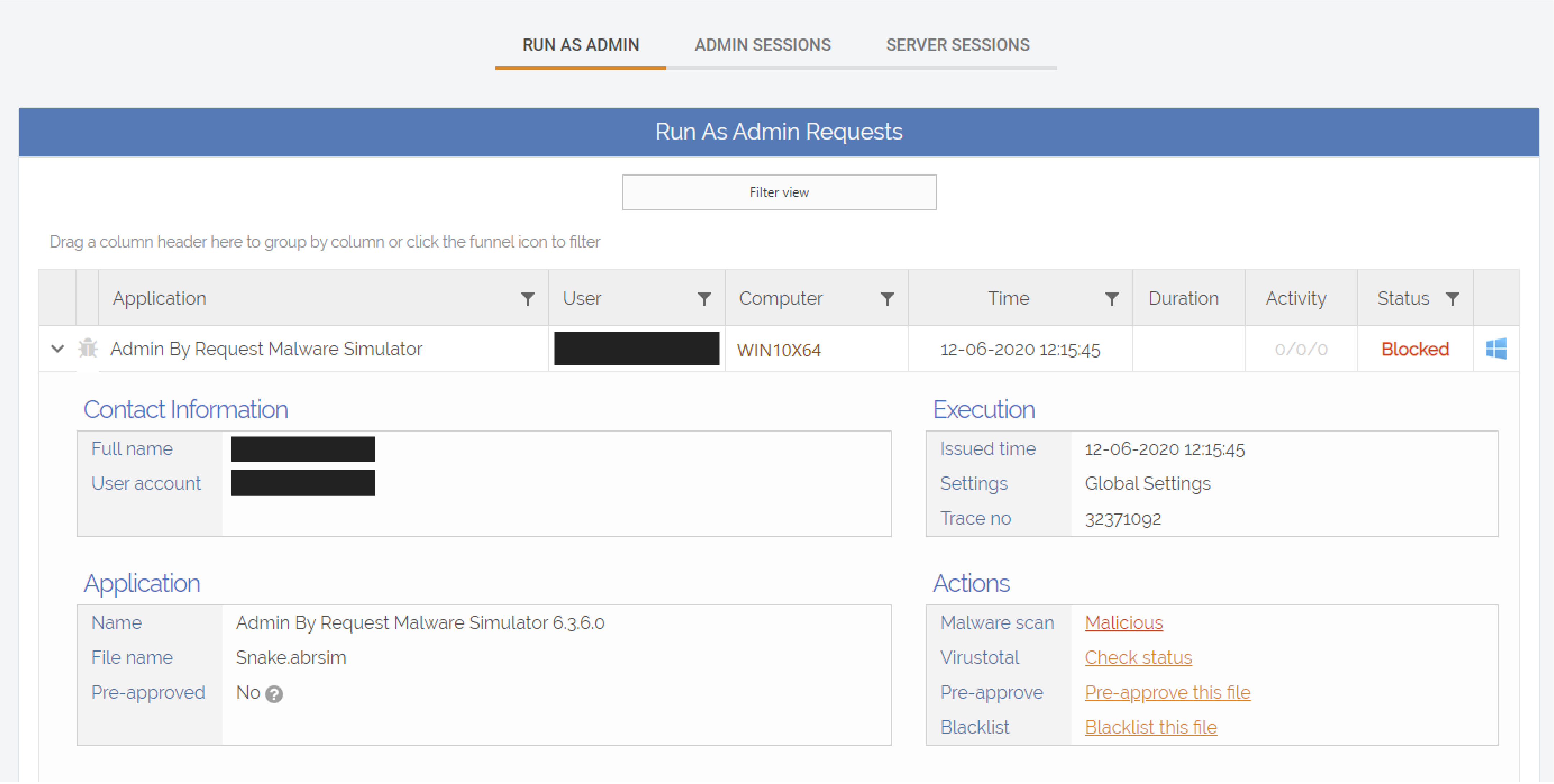
NOTE: The user details have been blacked out in these examples.
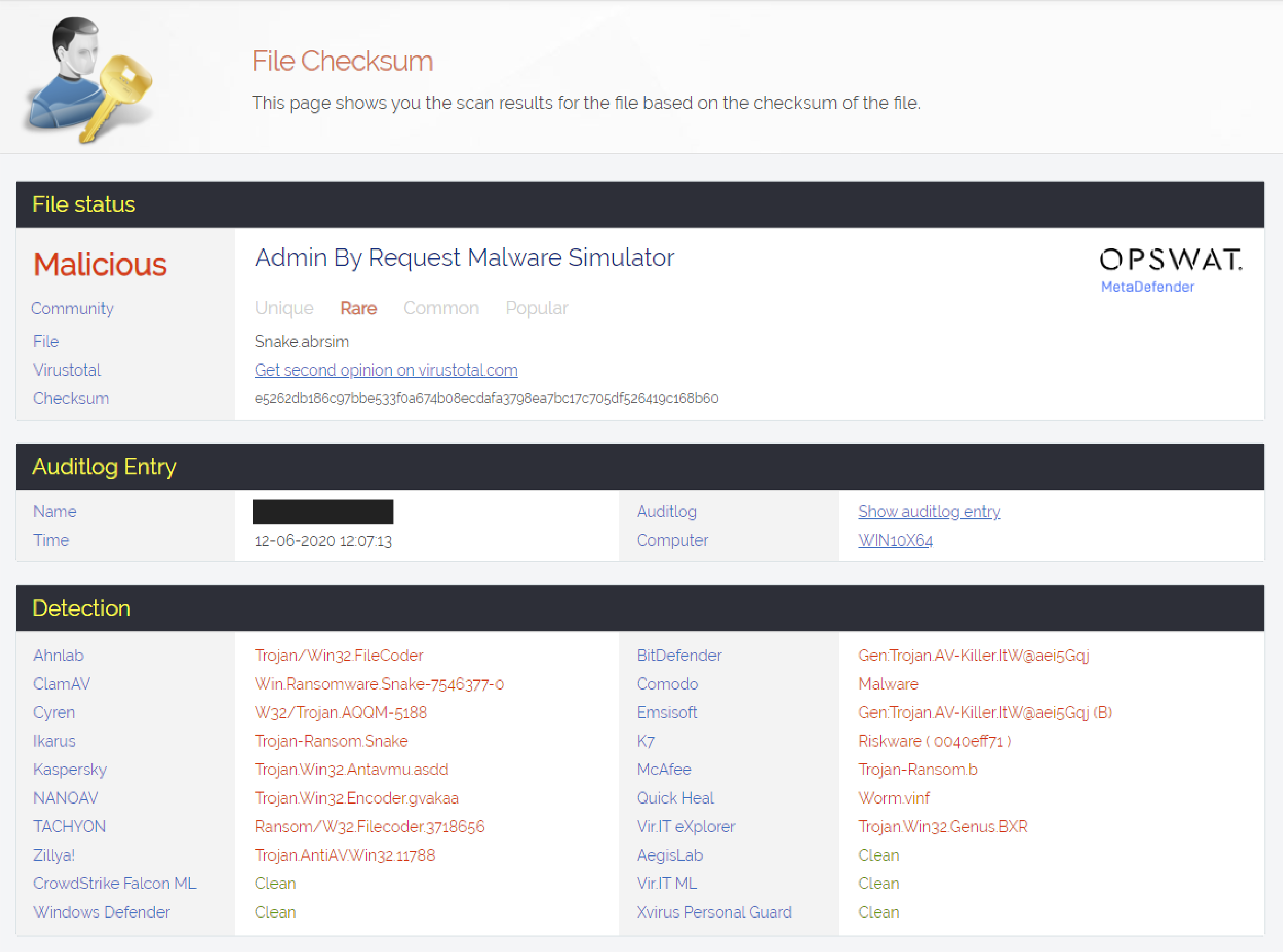
3. When you click on Malicious in the Actions section, Admin By Request takes you to a detailed view of what the malware scan picked up on the file:
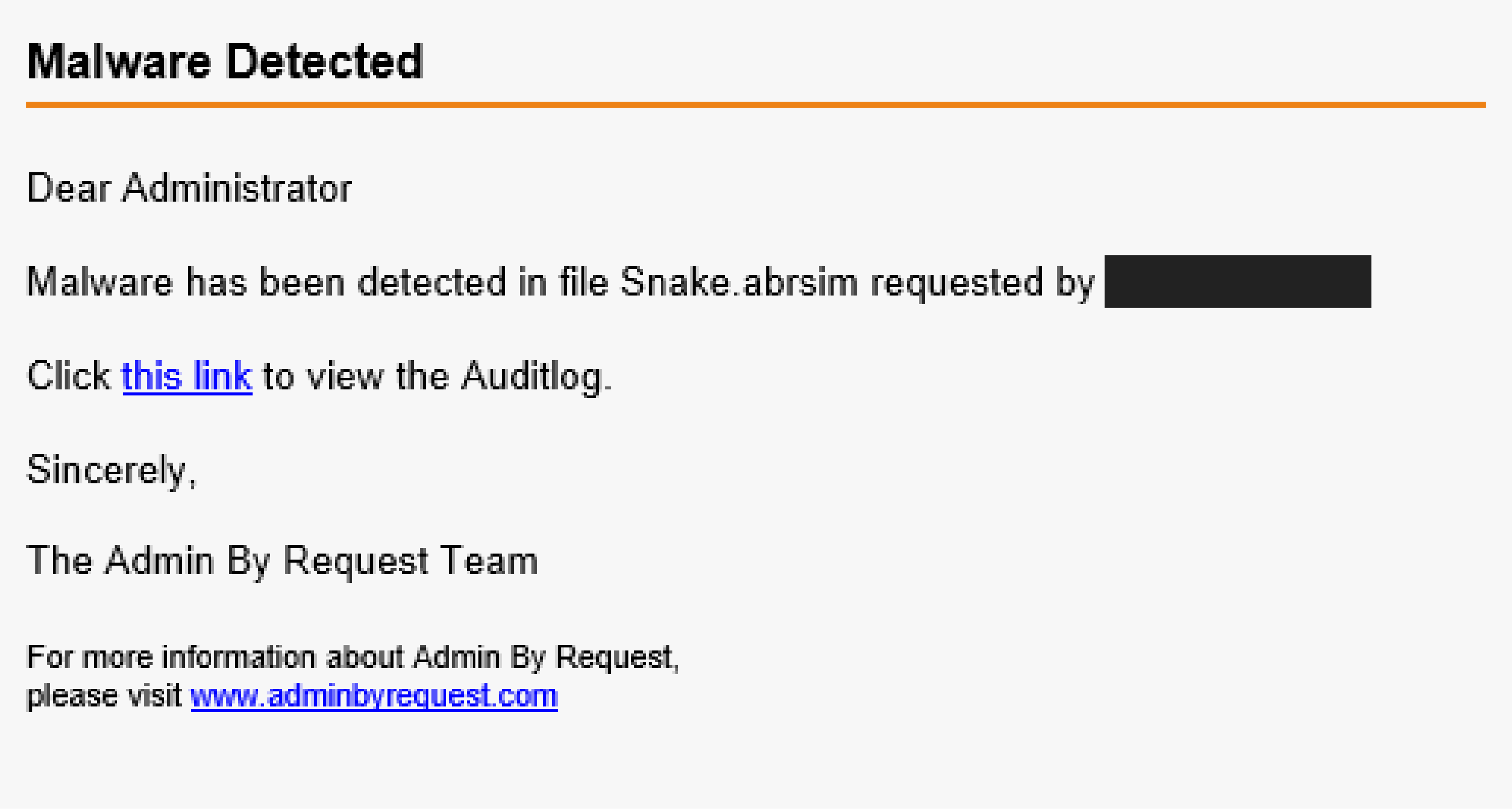
4. You, as the administrator, then get an email notifying you of the situation:
And that’s how advanced threat detection, combined with a PAM solution that records activity, makes it much harder for malware like Snake ransomware to get into your system – let alone gain administrator access.
Don’t Hiss Out
With ransomware now specifically targeting large, industrial organisations and having the ability to bring the production of these targeted companies to a grinding halt, the need for protection has never been greater.
Keep the snakes out of your boot, out from under your hood, and as far away from your network as possible with Admin By Request.







