It’s time to revisit the ransomware scene – a year on from our last encounter.
What’s it getting up to these days? Who’s running the show? Do they still have the upper hand, or are they losing some ground? Finding the answers to some of these questions might help us predict how the rest of the year is going to pan out, and what that means for us: the good guys.
Then vs. Now
In 2021 we took a deep-dive into Black Fog’s State of Ransomware Report, which gave us all the juicy details on attack numbers, target sizes, locations, and costs involved for ransomware in 2020 and 2021.
Looking at the same report, 12 months later, gives us a wider picture of what’s been happening while we’ve been gone:
- Number of Attacks per month are up – and have been on this trend for the past two years:
.png)
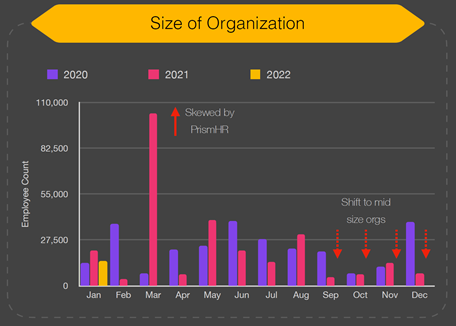
- The target-organization size on the other hand is continuing in the trend seen at the end of 2021, with the shift to mid-sized organizations:
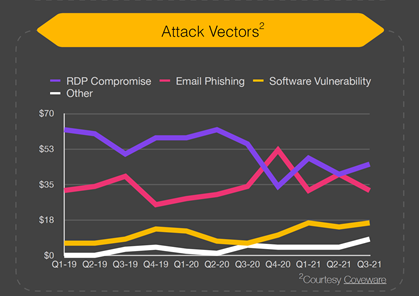
- RDP compromise, followed by email phishing, remain the top attack vectors:
Changes on the Scene
The data tells us that although infiltration tactics are staying the same, attacks are on the increase so far in 2022. So, what changes have we seen in the ransomware scene that have contributed to the rising numbers of attacks in January?
The ‘What’:
• Paying the ransom is becoming more common as organizations find themselves debilitated after ransomware attacks. In 2021, despite the ‘official’ advice from governments that companies do not meet the demands of cybercriminals, many large and well-known organizations paid staggering ransoms: CNA Financial, Colonial Pipeline, and JBS foods, to name a few. SophosLabs’ own State of Ransomware Report revealed that in 2021, the percentage of victims who paid up increased by 6%:
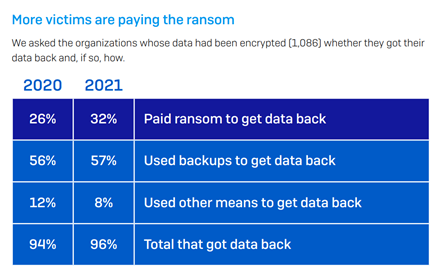
Image: SophosLabs’ 2021 State of Ransomware Report.
• Failure of ransom payouts to actually work. SophosLabs’ revealed that the average amount of data recovered after an attack and a ransom payout was 65%, with only 8% of the study’s participants getting all of their data back:
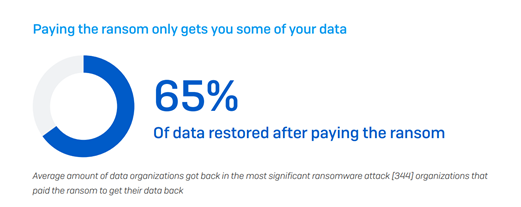
Image: SophosLabs’ 2021 State of Ransomware Report.
• Another change is the increased backlash from the public if a ransom is paid. It turns out the average Joe has become more judgmental over the past year. According to Forbes, paying a ransom breeds distrust, and a general feeling from consumers that the organization in question is to blame for the undesirable situation.
• A new tactic has emerged in the form of the ‘double-ransom’, thanks to increasing data exfiltration tactics. Instead of just encrypting your data, actors are exfiltrating it, so that if you have the nerve to refuse to pay a ransom to obtain a decryption key, they can blackmail you again with the threat of publicizing your data.
• Another noticeable change is just how noticeable ransomware attacks are becoming to the everyday consumer (you and I) due to specifically targeted attacks causing supply-chain disruptions. Where ransomware attacks were once a far cry from our everyday lives – something that the big companies had to deal with, and we only read about in the news – they’re now having far-reaching impacts that may affect our everyday lives. Take the Colonial Pipeline attack in May 2021: gas stations throughout the US had to close up shop due to the shortage of fuel – a direct result of supply-chain / industrial process disruption from a tactical ransomware attack.
The ‘Who’:
• While REvil has been a household name on the ransomware scene for the past few years, their future is in doubt coming into 2022. 14 members of the gang were arrested in mid-January by Russia’s domestic security agency – including the hacker who perpetrated the Colonial Pipeline attack mentioned above. However, aside from REvil, the other well-known gangs are still around and causing mayhem (DarkSide, Conti, BlackMatter).
The ‘How’:
• We know the tactics of infiltration have stayed the same over the past year (and beyond – when will people learn to monitor RDP ports sufficiently?), but there’s been a continuing shift in how ransomware gangs themselves operate, and it’s terrifying. The increasingly ‘professional’ and organized ransomware market is seeing the Ransomware-as-a-Service (RaaS) model on the rise from 2021: less skilled cyber actors can simply purchase or subscribe to existing ransomware tools or services, and then use the product to enact attacks as they see fit. What was once able to be achieved by only the most talented hackers out there, is now available to any Tom, Jack or Harriet.
• ‘Gentlemen’s Game’ is going out the window, with ransomware actors breaking unspoken rules left, right and center: there have been increasing attacks on the health sector, and, according to CISA, a tending towards attack-launches during weekends and holiday periods; when attackers know they will likely be able to able to do more damage before being detected.
• Another change in operations not seen before is the relations between ransomware gangs and bad actors. CISA points out that gangs have been networking more and more: sharing information about their victims with each other, including network-access information.
Predictions for the Future
In some industries, it’s never advisable to try and predict the future. The stock market, the housing market, the weather, to name a few. Cybersecurity does not fall under that umbrella. Predict, predict, predict, and predict the absolute worst!
The ransomware market is expected to continue on the trajectory we’ve seen at the end of 2021 and the beginning of 2022:
- Cybercrime organization and professionalism is going to keep improving, with ransomware gangs continuing to share data amongst each other and up the ante with the Ransomware-as-a-Service method.
- Ransoms will continue to be paid against government advice as organizations suffer – but the effects of doing so will start to have more of an impact, with their decreasing rate of effectiveness (in terms of recovering data), as well as the decreasing understanding and sympathy from consumers.
- Industrial processes and supply-chain operations will be targeting more heavily after the recent success seen in these areas – and we may well notice the impact in our everyday lives.
- Data exfiltration and the ‘double-ransom’ (another successful tactic) will be increasingly employed.
- Ransomware gangs and bad actors will stoop to new lows in terms of vulnerable targets and well-thought-out launch tactics. IT Brief notes that in 2022 we’re likely to see gangs targeting countries where they know they’ll receive less kickback, particularly after Russia’s crackdown on REvil.
In terms of our response to cybercriminals in the year to come, ZDNet reports that a ‘Paying to Prevent’ tactic may emerge, with organizations actually paying ransomware gangs a regular fee to ensure they don’t get targeted.
To combat the continuing meeting-of-demands by victim organizations, governments are likely to start cracking down on ransom payouts and begin to take more offensive action against gangs (what we’ve already started to see in Russia).
ZDNet also points out the potential impact on cyber insurance in the future. With ransoms regularly being paid into the millions; how much longer will ransomware attacks be covered by insurers? If insurance companies do continue to offer cover, premiums could reach new highs, and organizations seeking cover will likely have to jump through hoops to meet the eligibility criteria.
What to Do
For starters: DON’T start paying ransomware gangs to keep their mitts off you (talk about counterproductive!).
DO start implementing a zero-trust strategy. In fact, don’t just implement it: embrace it. Welcome it with open arms. Because we can make predictions until we’re blue in the face, but the one thing we know for certain is that if you haven’t implemented zero-trust, you’re at much greater risk of becoming victim to a ransomware attack.
Admin By Request is a cybersecurity solution which enforces zero-trust through the Principle-of-Least Privilege (POLP). It minimizes your organization’s attack window by instantly revoking all administrative access, and instead provides an application for Just-In-Time elevation, on an as-needed basis:
- All users become regular, protected users. When they need administrative access, they simply use the client to request the access they need.
- All admin sessions are logged, with attempts at privilege escalation (popular amongst ransomware actors) easily detected by the software’s alerting and Auditing capabilities.
Once ransomware actors infiltrate the system, they often rely on privilege escalation to succeed. With Admin By Request, infiltration in the first place is close to impossible, as all file downloads are scanned by multiple anti-malware engines. Attempts at privilege escalation are rendered fruitless as users simply don’t have the required admin rights. Hackers would have to vertically escalate to a more privileged status to make any ground whatsoever – an activity that would be detected immediately by the software solution if attempted.
Conclusion
It doesn’t have to be all doom, gloom, and warnings.
If anything, this blog is intended to be more of a friendly update – a check-in on the ransomware scene so that we can better predict where it’s headed in 2022.
Do yourself a favor and stay updated with what’s going on. Take the pre-emptive steps to get adequate protection, implement zero-trust with Admin By Request, and make sure you’re always one step ahead of ransomware gangs and their tactics this coming year.
I guarantee, this time next March – you’ll be grateful you did.
Did you know Admin By Request is free? Get it here for up to 25 endpoints.






