What if there was one anti-virus tool to rule them all, one anti-virus to find them? One anti-virus to bring them all, and in the darkness…? You get the idea.
Unfortunately, Tolkein’s Middle Earth had much fewer technological threats than what we are plagued with today, and a single anti-virus solution simply cannot find or bring, let alone bind, all of them.
Out with the Old: When the Battle Axe just doesn’t Cut It
Operating without some sort of malware protection is nonsensical, but just because you’ve got the latest version of Windows Defender and a fancy next-gen firewall installed, that doesn’t mean your organisation is fully protected.
Let’s take an in-depth look at the run-of-the-mill types of anti-virus available today, and why they may not be quite as effective as you think.
Traditional AV
Traditional anti-virus software works in the background of your system, taking notes on system files. It has a list of file signatures that it knows are malicious.
Typically, it detects malware using four techniques:
- Pattern Matching – A piece of malware is represented by a string of bits known as its signature. Pattern matching is the process of anti-virus software checking through each byte in a file and matching it to a byte in its list of malware signatures. If every byte in the file matches every byte in a signature, the anti-virus software will mark the file as malicious.
The downfall here is that the process relies on every single digit being the same. If just one bit does not match, the malware will evade traditional anti-virus software. Now that attackers are aware of this impediment, even miniscule mutations will bypass pattern matching processes. Newer threats such as “fileless” malware have no digital footprint and write nothing to the disc, therefore cannot be detected by pattern matching digital signatures at all.
- Heuristic Analysis – This technique considers the properties of the file and whether these fall within what it considers “abnormal”. It essentially has a set of rules or questions that it asks of the file, and if every rule/question returns true, the anti-virus flags the file as malware.
This heuristic approach fails by relying too heavily on its set of rules being 100% met in order to flag software as malicious. If the attacker gains knowledge that enables their software to not meet just a single rule, the malware will not be detected.
- Behavioural Analysis – This process works similarly to heuristic analysis but focuses on how the file behaves rather than its properties. If the behaviours match that of malware, the anti-virus will detect it.
This process takes a rather illogical approach as it requires the program to run first, before the anti-virus can detect malware. Here’s an analogy: imagine Aragorn, Legolas and Gimli monitoring the battle at Helm’s Deep to spot orc weaknesses, only to discover an entirely new threat, the Uruk-hai, arriving at their doorstep. Better late than never?
- Hash Matching – A hash value can be generated by running a file through an algorithm, such as MD5 (Message-Digest algorithm) or SHA-256 (Secure Hashing algorithm, 256 bit). Anti-virus software calculates these hashes and compares them to hash values of malware. If the hashes match, the anti-virus will detect malware.
This has drawbacks similar to pattern matching – the changing of a single bit on any part of a file used to generate the hash value will generate a completely different hash value and the anti-virus software will fail to detect malware.
Furthermore, the hashing algorithms used to produce hash values have been proven unreliable. A requirement of a hash algorithm is that it is illogical to find two inputs that produce the same hash (known as collisions). MD5 is known to have such vulnerabilities, this having been proven in 2012 by Flame malware, making this technique an unreliable one for anti-virus software to use. SHA-256 has also been found to produce collisions, although not to the extent of MD5.
A third point of weakness is that hash matching is futile against polymorphic malware, which is malware that continually changes its features in order to remain undetected.
The major fallback of traditional anti-virus is its inability to detect software that it has not encountered before. It relies on matching malware with known software in its database, making it ineffective at detecting zero-day malware (malware that has not been previously encountered). This is explained more fully in the ThreatVector article How Traditional Anti-virus Works.
Artificial Intelligence and Machine Learning Anti-virus
Traditional anti-virus software has been improved with Artificial Intelligence and Machine Learning anti-virus solutions.
Artificial Intelligence (AI) is a program that can “mimic” human intelligence. Machine Learning (ML) is a subset of AI, where the machine “learns” as it is exposed to more data, allowing its response to improve over time.
AI-based anti-malware is ideally able to recognise malicious software when it hasn’t been previously identified, and/or before it is able to execute. Machine learning programs can learn beforehand what is considered normal behaviour and are then able to identify anything that may fall outside of this, enabling pre-emptive defence against malicious software. The new threat can then be added to the anti-virus engine’s existing database.
AI-based anti-virus software is helpful against zero-day attacks and identifying malware that has been slightly modified in order to escape detection by traditional anti-virus software, as it relies less on known digital signatures and a set of rules, and more on how software behaves.
Although advancing all the time, AI and ML anti-virus solutions are not the be-all and end-all. Here’s how an AI/ML-based system could be fooled:
- Exploiting the model – ML anti-virus software is given large amounts of data and left to process and make decisions on this data based on the parameters within its model. If an attacker can find out how the model uses its parameters, they could exploit the model by changing something within a file that they know will trick the model into thinking it is safe.
Take for example Cylance’s AI anti-virus software, which was duped in 2019. Researchers were able to discover a bias in Cylance’s ML model towards a particular game that the model had whitelisted (marked as safe). They exploited this weakness by appending non-harmful strings of code from the game to a malicious file. The researchers, from Skylight Cyber in Australia, trialled this technique with 384 malware programs, with Cylance’s detection rate being less than 11%.
- An imperfect dataset – ML algorithms use the dataset they are provided with to learn: the more data provided for the program to learn, the more effective it will be at doing its job.
However, an effective model requires all the data to be labelled correctly. If one data input is labelled incorrectly, the machine could use this particular input to form a bad decision that it then builds on as part of its learning, resulting in an ineffective model in the long term.
Sandboxing
Sandboxes are used to run potentially malicious material in a tightly controlled environment with restricted network access and inability to read from input devices. A sandbox is often used to run untrusted or untested software and, because it is isolated from the host device, it can stop the spread of malware to the rest of the machine.
This particular security mechanism analyses an object’s behaviour as it executes, which makes it helpful in detecting malware that may have passed under the radar of other anti-virus programs while static.
Although a security favourite, sandbox technology has its downfalls.
One of its security measures is also a downfall. The tightly controlled sandbox environment can often be a dead giveaway for malicious software. Hackers can program malware to recognise when it’s running in a sandbox environment, at which point it will terminate or, in more sophisticated programs, perform fake operations in order to appear benign, until it is marked as safe by the sandbox and delivered to the host device.
Another sophisticated way through a sandbox is in delayed execution. As sandboxes are used temporarily to test and check software before allowing them onto a host device, attackers can program delays into malware so that it doesn’t execute until an amount of time has passed (enough time for the sandbox to have performed its analysis) or certain operations take place, such as a restart. In the same case as above, sandboxes can fail to detect malicious behaviour and pass the malware to the host device, where it will later execute.
Malicious software that is packaged within clean files often goes undetected by sandboxes, as does encrypted malware, which (unless decrypted) is simply invisible to security systems.
Password-protected emails containing malware are often passed on to the end user by sandboxes as they cannot gain access to analyse it.
Some programs simply cannot run in a sandbox environment due to the restrictions in place, so malware within these programs evades sandboxing systems completely.
Although you wouldn’t want to ride into Isengard without a sandbox at your side, make sure it’s not the only thing in your arsenal – sandboxes do have several vulnerabilities that can be exploited by attackers.
In with the New: From Battle Axe, to Many-Handed Longsword
Now, imagine a tool where all these solutions are covered in one. This is where Opswat MetaDefender comes in. The name speaks for itself:
- META: Most Effective Tactic Available. The best way to win the game. A specialised form. Seeing from a higher perspective. Going above and beyond.
- Defender: …let’s assume you know this one.
The MetaDefender provides a multi-layered approach, encompassing a multitude of security modules, rather than a single anti-virus engine or sandbox solution.
Let’s break these layers down and discover how MetaDefender triumphs over other anti-virus technologies, starting with (bring in the war-drums please…) :
The MetaDefender Core
The MetaDefender Core integrates six security modules to form a comprehensive anti-virus solution that can be used on-premises, in the cloud, and with air-gapped networks.
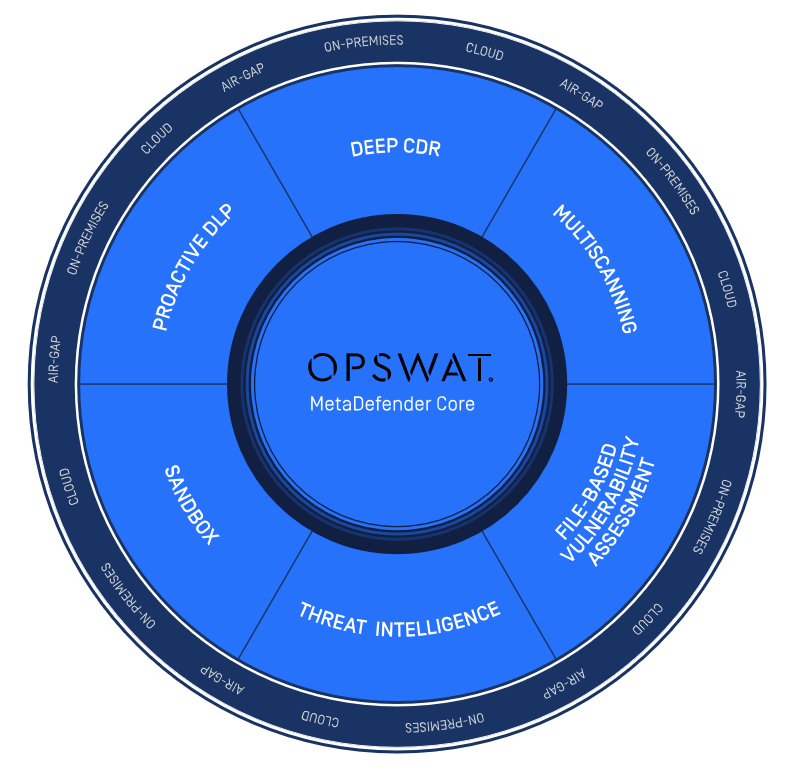
Here’s how it works:
Multiscanning
MetaDefender makes use of 35+ anti-malware engines when it scans files. These engines use a combination of traditional and AI/ML tactics, such as digital signatures, heuristics, and ML models, to detect known malware files.
We know why relying on a single anti-virus program to detect all threats is a mistake. MetaDefender knows this too, so has partnered with over 35 anti-malware companies which are all used to scan your files with Opswat’s multiscanning module to make sure no threat slips through unnoticed.
35 rings of power are better than one, right?
Deep CDR
Standing for ‘Deep Content Disarm and Reconstruction’, this security module boasts the motto “Trust no file” and assumes that every file is malicious. It identifies file types and scans them using its multiscanning tool.
It then implements the CDR process of breaking the file down and reconstructing it, removing malicious elements and preserving the usability of the file. Voila: you now have a new, safe file to use, while the other is quarantined.
Deep CDR is effective against zero-day attacks and prevents threats that may slip past other anti-virus technologies, as it disarms and rebuilds all files under the assumption that they are all evil.
Proactive DLP
MetaDefender takes protection a step further with its Proactive DLP (Proactive Data Loss Prevention) module, which redacts PII (Personally Identifiable Information) found in files being uploaded, protecting organisations from potential (and expensive) compliance violation risks.
File-based Vulnerability Assessment
Vulnerability scanning is a process which detects weaknesses within a network or on a computer. Yet another step organisations must take to ensure they stay protected from hackers.
Again, MetaDefender has this base covered with its file-based vulnerability assessment module.
While most vulnerability scanners identify exploitable points after software has been installed, MetaDefender can get it done before installation. It can also scan for vulnerabilities while programs are running, or at rest.
So far, we’ve killed… four orcs with one arrow? Yes please.
Threat Intelligence
Recall those times when you’ve run a “quick” anti-virus scan of your device and it ended up taking three full moons, a few winters, and the dawning of a new age …
Anti-virus software relies on data to do its thing: matching signatures, hashing, behaviours, and a bunch of other security intel. There is so much activity going on during these traditional scans that computers can become unusable during the time it takes. If your anti-virus software had a smaller dataset, the process wouldn’t be quite so tiresome, but it also wouldn’t be anywhere near as effective.
Incoming: cloud-based threat intelligence. Put the dataset on the cloud, and Boom! – you won’t be growing a full beard in the time it takes to perform a scan.
MetaDefender’s threat intelligence platform has an expansive cloud-based database, developed from analysing data from thousands of computers worldwide, offering “one of the fastest file hash lookup services in the market” (3.86 seconds to scan a file and 15 milliseconds to look up a hash, FYI).
A huge dataset and no performance issues on your device, that’s another orc in the bag.
Sandbox
Just to add an extra layer of chainmail, the MetaDefender Core also integrates a sandbox environment.
How many orcs are we up to now? I’ve lost count.
Forging the Ring: Putting it All Together in a PAM Solution
The Dangers of Running as Administrator
So, when do organisations run the most risk of coming face to face with the enemy, aka: malware? When they give too much power to the end user via administrator rights.
Admin rights are a powerful thing and are not to be taken lightly; we all know what happens when one gets tempted by power …
The majority of malware infections within an organisation result from end-users having administrator access to their computers. Aside from being able to install and execute malicious software, admin rights allow an individual to:
- Install unauthorized software that may slow down computer systems or lead to non-work activities (stop playing solitaire Jeff! Unless it’s LOTR-themed, in which case it’s acceptable).
- Install unlicensed software that may result in fines when software vendors come knocking.
- Access other user profiles and data, leading to potential privacy beaches, data breaches and theft.
- Make changes to the operating system settings, which may cause a myriad of problems and be costly to fix.
But, although dangerous, admin rights are a necessary evil. The answer is simply to control the evil, with PAM: Privileged Access Management.
PAM to the Rescue!
PAM is the strategy of controlling user access and permissions across an organisation’s IT infrastructure. The main goal is to operate in an environment of “least privilege”: restricting access and permissions to the absolute minimum necessary for users to get their jobs done.
We know that admin rights open the doors to the danger zone in computer systems. Administrator accounts are targets for attacks due to their privileged rights: elevated permissions, access to sensitive information, and the ability to change OS settings. In fact, according to Forrester Research, privileged credentials are involved in 80% of data breaches.
With a PAM system in place, organisations can control who is accessing what, log everything being accessed/downloaded/installed, monitor any suspicious activity and segregate their networks. This enables businesses to crack down on the small stuff (Jeff and his solitaire addiction) and reduce their computer systems attack surface (the big stuff) without hampering productivity.
An Ode to the Fallen: Moller-Maerske
Let’s talk about this “big stuff”.
We know that users with privileged credentials can install and run dodgy files and programs. Of greater significance is their ability to access other user profiles and data and make changes to the operating system settings because of their privileged credentials.
To grasp why this is significant, one only has to ask Moller-Maerske: the world’s largest container shipping company, which was brought to its knees in 2017.
NotPetya ransomware is thought to have originated in a Ukrainian company’s accounting software called M.E.Doc during an auto-update, and it got its foothold in just one computer in a Maerske branch in Odessa, Ukraine, when an employee requested IT admin to install the M.E.Doc software on his computer. NotPetya spread swiftly across Maerske’s entire international computer system, moving laterally across the network by extracting administrator credentials. The ransomware (or “wipeware”, being the more appropriate term for the destructive software) took down Maerke’s entire network of 4000 servers and 45,000 computers, resulting in $300,000,000 in damages to the Danish company.
Read the full story here: The Untold Story of NotPetya, the Most Devastating Cyberattack in History, and get the all the technicalities here: NotPetya: Timeline of a Ransomworm.
How did a company that was not the target of the attack, but was simply caught in the crossfire, allow this to happen? The previous year, Maerske IT executives had raised concerns about out-of-date operating systems, poor patching and, above all, lack of network segmentation (i.e. dividing a network into smaller parts so that one area/set of users do not have access to others). Had Maerske implemented better network segmentation within their infrastructure, they may have been able to contain the spread of NotPetya ransomware.
And how can network segmentation be achieved? Through PAM. BAM! (standing ovation please).
The Ring of Power in the Right Hands: Admin By Request
What do you get when you cross Opswat’s MetaDefender with Admin By Request’s PAM solution? Basically, a Gandalf-Aragorn hybrid that even the Witch-King of Angmar can’t beat.
Admin By Request has partnered with Opswat to bring you the ultimate security tool with their MetaDefender Cloud.
Many solutions rely on an administrator spending endless amounts of time whitelisting programs or doing remote installs, but Admin By Request works the other way around: intercepting software installs made by users and installing it without the user being an administrator. See how it works here.
No remote installs necessary and no need to be constantly updating whitelists leads to a very grateful IT department.
Mitigated vulnerabilities from not having admin accounts left, right and centre leads to a very safe computer network.
Combine this PAM solution with MetaDefender’s 35+ anti-virus engines, and the chances of your system being compromised are virtually zero.
Fun fact: Bitdefender and Avira anti-virus solutions are often 100% effective against malware. Both of these engines are part of the 35+ that supply the MetaDefender Core.
Opswat’s Detection Efficacy overview provides more of an insight into just how well the Multiscanning module does its job: 4 engines detect 62.80% of the top 10,000 searched for threats from the MetaDefender Cloud database, 12 engines detect 90.53%, 20 engines detect 98.69%, and the MetaDefender Cloud detects 99.02%.
To put it simply: Jeff may not have a valid reason for installing LOTR-themed solitaire onto his work computer, but at least you can rest assured knowing it’s safe.
See how Opswat is implemented by Admin By Request: Admin By Request – Malware Detection.
Epilogue
In Opswat’s words:
“Single anti-malware engines, next-gen firewalls, sandboxes, machine learning, IPSs, and proxy anti-malware solutions do not provide adequate cybersecurity protection on their own”.
Can one anti-malware solution really rule them all?
Absolutely, if it combines an array of anti-malware tactics and an ingenuitive PAM solution into one war-effort. Download it here.
Take that Sauron.







