Regardless of whether your business is big, small, or somewhere in between; in the health, technology, hospitality or transportation sector – if you get hit with a data breach, it’s going to cost you money.
And with businesses worldwide being affected by the economic fallout accompanying the Covid-19 pandemic, the last thing any organization needs is a costly data breach.
Data Breach Basics
A data breach is a security incident in which an organization’s sensitive or confidential information is accessed, viewed or exfiltrated by an unauthorized individual.
Data breaches are always going to cost money to investigate, remediate and recover from – but just how much money are we talking?
IBM’s 2020 annual Cost of a Data Breach Report delves into the details.
The Stats Summed Up
Here are a few of the findings at a glance:
- The average total cost of a data breach for 2020 was $3.86 million USD. Although this is a slight decrease from 2019 (%3.92 million), the total average has increased by 10% since 2014, from $3.50 million.
.png)
IBM Cost of a Data Breach Report 2020 – Figure 2
- The average total cost of a data breach at companies with more than 25,000 employees was $5.52 million USD. The average total cost for these large enterprises was almost $3 million higher than the $2.64 million average total cost for organizations with fewer than 500 employees.
- The average time to identify and contain a data breach is 280 days. Companies on average required 207 days to identify the breach and a further 73 days to contain it.
- 52% of breaches were a result of a malicious attack. Of these malicious attacks, 53% of breaches were caused by financially motivated cyber criminals, 13% each were hacktivists and state-sponsored hackers, and 21% remained unknown, with the average total cost of malicious attacks sitting at $4.27 million.
- The costliest malicious breaches were caused by state-sponsored attackers. Breaches by nation state actors had an average total cost of $4.43 million USD, versus $4.23 million for breaches caused by financially motivated hackers.
- Remote working is expected to increase the time to identify and contain a data breach by 76%. Of the companies that required remote work in response to Covid-19, 76% believed it would increase the time taken to identify and contain a data breach.
- Remote working is expected to take the average total cost of a data breach up to $4 million USD. Of the companies that required remote work in response to Covid-19, 70% believed it would increase the total cot of a data breach. In addition, having a remote workforce was found to increase the average total cost of a data breach by almost $137,000.
- Stolen or compromised credentials were the most expensive cause of malicious data breaches. 19% of companies that suffered a malicious data breach were infiltrated due to lost or stolen credentials, taking the average total cost for these countries up by almost $1 million, to $4.77 million.
- 12 out of 16 countries showed an increase in total cost from 2019 to 2020. The United States experienced the highest average total data breach costs in the world, at $8.64 million.
- The largest contributing cost factor to the total cost of a data breach was loss of business, at 40%. Including increased customer turnover, lost revenue due to system downtime and the increasing cost of acquiring new business due to diminished reputation, loss of business accounted for $1.52 million of the average total cost of a data breach in the 2020 study, compared to $1.42 million in 2019.
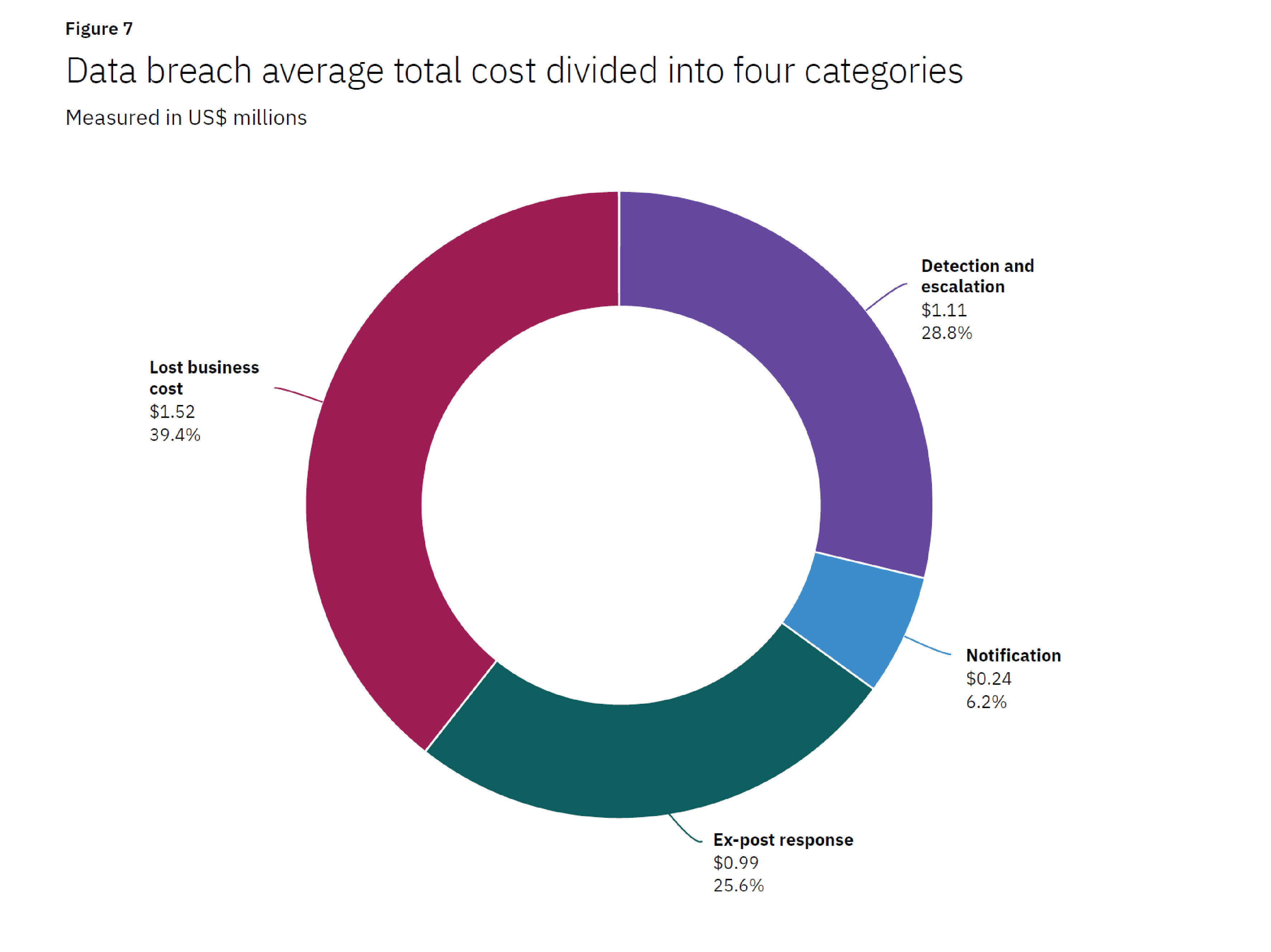
IBM Cost of a Data Breach Report 2020 – Figure 7
Putting the Data into Perspective
If your organization suffers a data breach, you probably won’t know about it for over 200 days – by which point, the damage that’s going to cost you will be well and truly done.
The cost of such a breach will more than likely set you back upwards of 3 million dollars (or closer to 5 million if your company has more than 25,000 employees), predominantly due to business lost while trying to recover from an attack.
Although a slight decrease from last year, the total cost shows a considerable increase in the past 6 years, with Covid-induced remote working (something that isn’t going anywhere any time soon) sending both the likelihood of a breach and the total cost soaring.
Malicious attacks are making up more than half of data breaches, with the costliest of these coming from well-equipped, state-sponsored hackers; and of these malicious attacks, the most expensive cause is lost or stolen credentials.
It’s Not What you Know, It’s How you Act
Knowing the statistics of how much a data breach is likely to set you back by is a useful thing.
But knowing how to prevent such a data breach in the first place and save your organization millions of dollars is considerably more useful.
- Malicious attacks from both financially motivated cyber criminals and highly trained, well-equipped, state-sponsored hackers are a big contributor to the data breach problem.
So, to effectively avoid a data breach and the cost that comes with it, you need to ensure that no hacker, regardless of their intention, can gain access to your organization’s wider IT environment and sensitive data.
The best way to do that is by protecting your privileged user accounts.
The higher the privileges of a user account, the more valuable that account is to malicious hackers.
This is because privileged user accounts enable those who have access to them to do things that can affect other users and the entire computer network, meaning they give attackers a much wider reach to view, copy and steal sensitive data within an organization’s network.
For that exact reason, bad actors often seek to compromise a network via local administrator accounts, or attempt to gain elevated privileges from a regular user account (a technique called privilege escalation).
Stop malicious attackers from doing this and you might just prevent a $3 million dollar data breach.
Easier Said than Done.
With Admin By Request, preventing data breaches is gloriously simple – even for enterprises of 25,000+ employees.
Combining a Privileged Access Management (PAM) solution with a comprehensive anti-malware Cloud API, Admin By Request effectively closes the doorway that is the end user.
PAM software allows an organization to manage, monitor, control and audit privileged user access.
It effectively protects the network from data breaches by using Just-in-time elevation (JIT) and the Principle of Least Privilege (POLP) to ensure users are only able to gain elevated privileges on their machines when absolutely necessary; they otherwise operate with the least privileges required to do their jobs.
Admin By Request implements JIT and POLP by revoking local administrator rights, requiring user’s to instead make a request to a company IT admin when they need to operate with elevated privileges.
Requests can be approved or denied, and files installed when a user request is approved are scanned by OPSWAT MetaDefender’s 30+ anti-malware engines to ensure no malware can make itself at home on your system – for an average of 280 days before detection and containment is achieved, according to the Report.
To successfully breach an organization’s network protected by Admin By Request, hackers must first successfully escalate from a non-privileged user account undetected: an essentially impossible task with the PAM software’s audit trail logging every action taken by a user operating with temporary escalated privileges.
A Pre-Emptive Strike
The price of preventative cyber security software doesn’t even come close to the cost of recovery if you fail to implement security measures and suffer a costly data breach.
With Admin By Request, you can close the door on all manner of malicious attacks and avoid having your organization become part of the increasingly alarming data breach statistics. Download the Free Plan today to get started.







