To embrace the increasingly necessary zero-trust model, implementing a Privileged Access Management (PAM) solution is a must.
Admin By Request provides an enterprise SaaS in the form of a comprehensive PAM solution – all offered as part of a free plan.
Overview
An effective PAM solution needs to protect every enterprise endpoint that has access to your companies’ network and data.
It should provide the functionality to manage your local administrators, report changes in the local administrator’ group, monitor event logs and alert you to suspicious activity.
Admin By Request’s free plan contains every feature that forms an effective PAM solution.
It revokes your user’s local administrator rights and instead provides on-demand application elevation, only when absolutely necessary.
Admin By Request’s free plan also offers malware protection – a required feature when it comes to meeting the minimum cyber security compliance requirements.
Read on for a closer look at some of the main features.
Main Feature Spotlight
A Refined UAC Experience
The core function of any PAM solution is to manage privileged user access.
Admin By Request’s system for granting elevated access is essentially an improved, refined and more encompassing version of the unpopular-but-necessary Windows User Account Control (UAC).
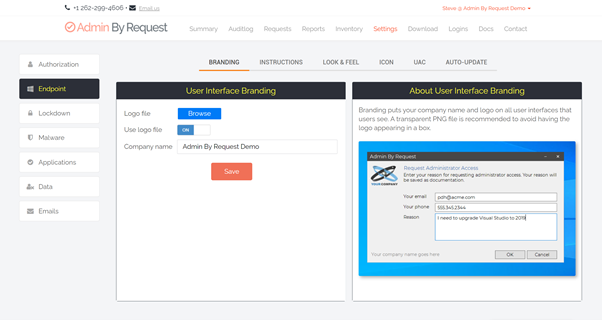
When a user needs elevated access, our customized version of UAC’s Consent UI displays the Admin By Request client’s Confirm pop-up to the user.
The Confirm pop-up is the default for our software, but you have the option within the Admin By Request user portal Settings to make this an Authenticate pop-up, which requires local admins to enter their credentials before they are able to continue.
.png)
The Settings in your user portal also provide the option to:
- Require Reason. The user must type in a reason for their request for elevated privileges, and
- Require Approval. The request gets sent to the Requests page in the Admin By Request user portal, where it must be approved by an IT admin before the user can proceed.
More on Settings further down.
Elevating Processes, Not the End User
An integral feature of Admin By Request is the way in which on-demand privileged access is provided, without compromising security.
This is achieved by granting elevation to applications rather than user accounts – meaning the user never gains full administrator access to the system.
Pre-Approval of Applications
Our version of whitelisting, this feature gives you the ability to add trusted programs to your pre-approval list, so that your users don’t get interrupted unnecessarily with UAC prompts for applications known to be safe.
Learning Mode
This feature enables you to gather the appropriate data on what programs are being run as administrator before you fully revoke user’s admin rights.
The information gathered during Learning Mode will hep you identify which applications should be added to your pre-approval list, and which should be blacklisted.
Extensive Logging
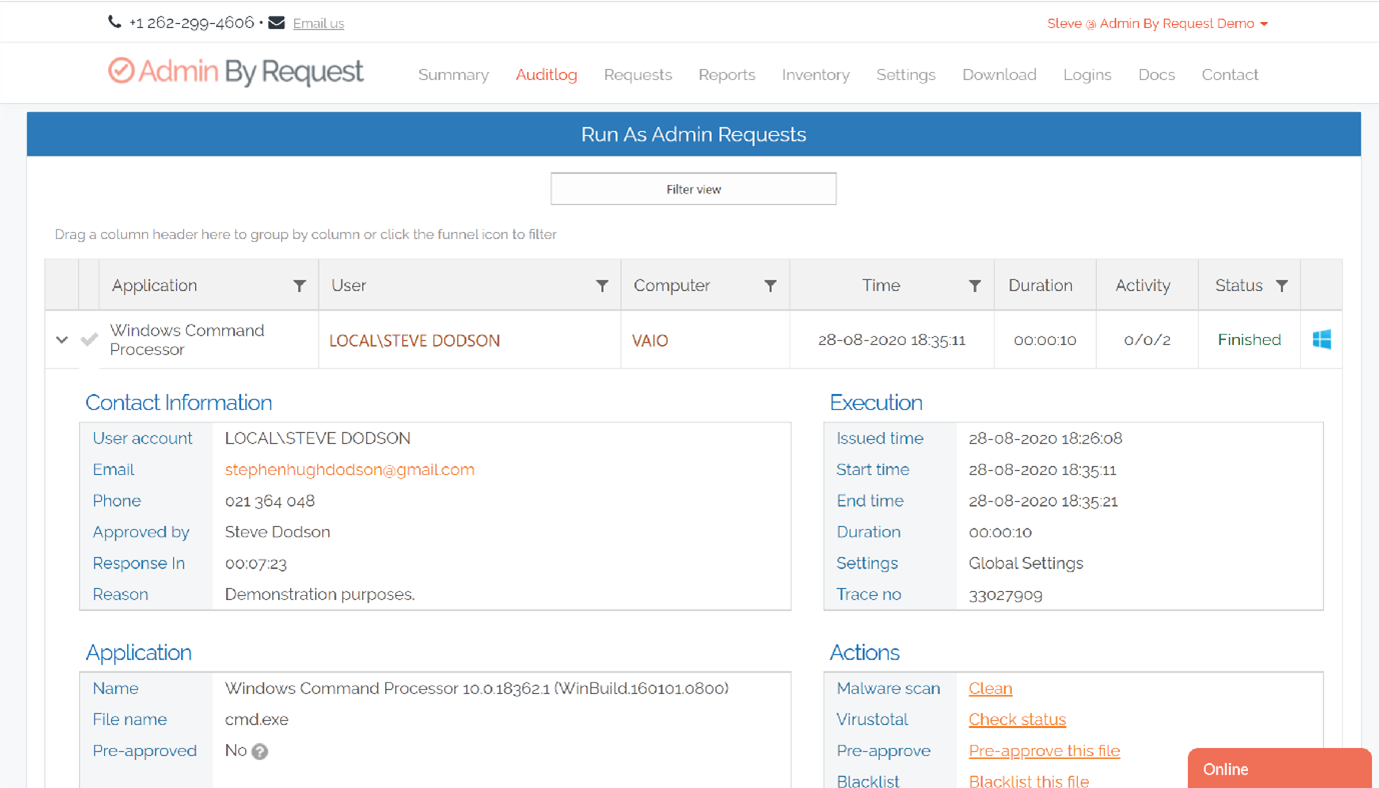
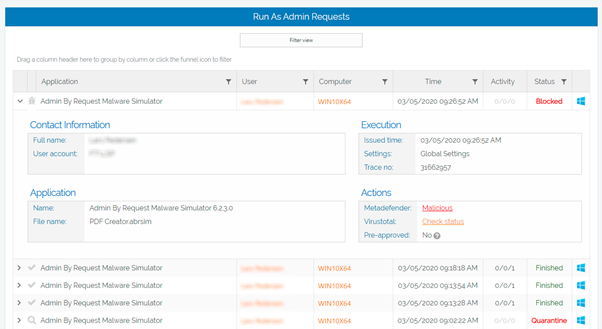
Within the software’s online user portal you’ll find the Auditlog, which lists every occurrence of your user’s privileged access sessions.
Expanding each list item reveals a comprehensive collection of information logged during that session, such as the user’s contact information, software that was installed and uninstalled, and programs executed using elevated privileges.
User-Friendly Reporting
The Reports feature in the Admin By Request user portal collects and displays key pieces of user, inventory, malware and activity data.
Information collected in the Reports section includes where your devices are located, user elevations, malware detections, new computers, and hardware & software inventory.
Information collected on Activity includes API activity, login activity and changes to settings.
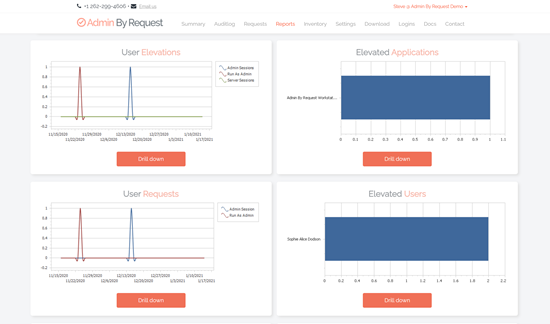
Reports Dashboard
Fully configurable, the Reports Dashboard presents key data at a glance in the form of user-friendly charts, allowing you to configure the timespan of displayed data.
Malware Detections
The Reports feature includes comprehensive reporting on malware detections, thanks to OPSWAT’s MetaDefender Cloud.
More on malware detection further down.
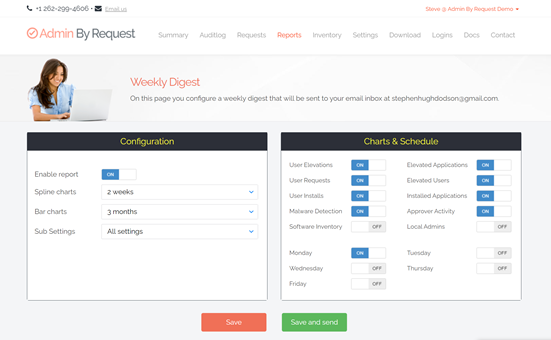
Weekly Digest
Admin By Request provides a customizable Weekly Digest feature, which gives you the ability to configure what reporting data is displayed, the timespan of this data, and when/how often it gets sent to your inbox. You can test in the free plan using the button at the bottom of the report dashboard page. But it is not fully available in the free plan.
Collection of Inventory Data
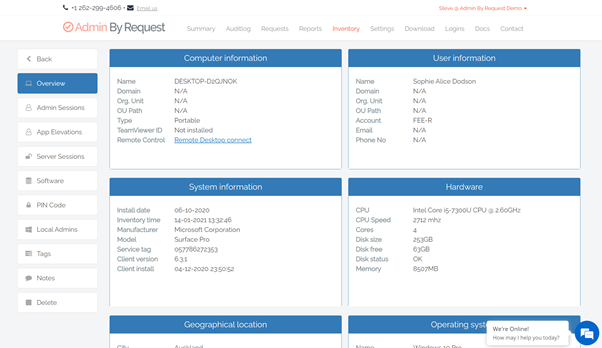
Each device on your network that has Admin By Request deployed will appear in the Inventory list.
Collected inventory includes the device’s name and domain, the user’s email address and phone number, the computer manufacturer, model, geographical location, and more.
Customizable Settings
We understand that every enterprise is different and therefore, flexibility is a key feature of Admin By Request’s PAM solution.
Within the Settings page, you can configure everything from the UAC experience (mentioned previously) to user interface branding and appearance. You can determine what personal data is collected, specify how your malware detection operates on your endpoints, create your own email templates, and more.
Protection from Malware
Malware Detection features heavily in Admin By Request – because we know that a single, endpoint anti-virus solution isn’t enough to adequately protect your network from malware.
Our PAM solution is integrated with OPSWAT’s MetaDefender Cloud, which scans files in real time with over 35 anti-virus engines.
A file flagged as malicious is prevented from doing any damage and logged in the Auditlog.
You then have the option of using the built-in Virustotal check on the file and undertaking further actions.
More information on our Malware Detection feature can be found here.
Mobile Application
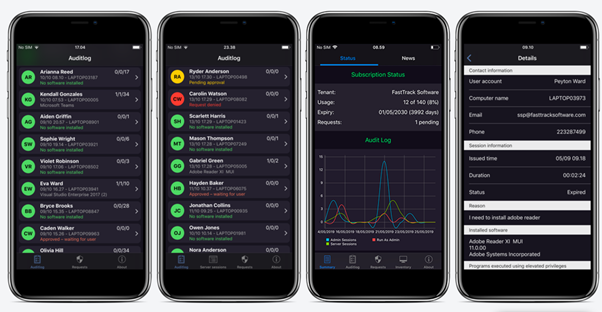
Admin By Request’s free plan includes access to our mobile application, from where you can approve or deny user requests for elevation, view the auditlog, adjust settings, and access everything else in your user portal – all from your pocket.
Versions for Different Operating Systems
We recognize the need for MacOS cyber security just as much as Windows.
With Admin By Request’s free plan, you can download and deploy the software solution to either or both operating systems.
Quick, Easy, and Unintrusive
Despite the long list of features that come with our software’s free plan, deployment is short and sweet.
Once deployed, users will be none the wiser that they have lost their local admin rights – they can continue as they always have with Admin By Request silently standing guard in the background.
What’s not in the Box?
You get a lot of bang for your buck with our free plan, but there are a select few differences to note between free and paid.
We generally offer our free plan for up to 25 endpoints, but don’t despair if you don’t meet the 25-endpoint limit – get in touch with us and we can have a chat.
The paid version of Admin By Request offers a comprehensive Support Assist feature that we don’t supply with the free plan – more details on Support Assist can be found here.
Also with the unpaid plan, licenses are retained rather than released immediately.
Summary
We’ve highlighted some of the key features that make our PAM software’s free plan a comprehensive, user friendly and flexible option for your enterprise.
Head to this page to get started – and enjoy a secure network with Admin By Request.







