RDP Basics
For RDP-newbies, read on for the absolute basics. (Otherwise, see Microsoft’s documentation for a detailed breakdown on how the connection works.)
What Is It?
As the name suggests, Microsoft’s built-in Remote Desktop Protocol (RDP) allows for remote access over a network connection from one computer to another.
It works by opening a dedicated channel on the default RDP listening port (3389) over which data packets – including keystrokes, mouse movement, and desktop display – are sent, via Transmission Control Protocol and Internet Protocol (TCP/IP).
With a successful RDP connection, comes full access to the remote device, including its files, network, and servers; and this access grants the user complete remote control. Handy! …or dangerous? We’ll get to that.
History
It’s been around since the mid-90s, created by software company Citrix and eventually introduced in 1998 as ‘Terminal Services’ in Windows NT 4.0 Terminal Server Edition, with the purpose of giving non-Windows and terminal users the ease of use and benefits of Windows; previously unavailable Windows-based applications could be displayed and interacted with on remote clients following execution on a server.
Common Use Cases
Its original goal of providing powerful capabilities to less capable computers still stands today, however common use-cases have expanded to include:
• System administrators providing all manner of assistance and maintenance to less tech-savvy staff from the comfort of their ergonomic desk chairs.
• Employees accessing corporate devices remotely while away from the office, be that due to traveling or – the more likely scenario in light of the ongoing pandemic – Working From Home (WFH).
The second scenario has become the more prominent use for RDP, with forced WFH leading to the normalization of teleworking.
The Dangers
There’s no arguing that RDP is pretty handy at the very least, and remarkably powerful at best. But as a wise man (a.k.a. Uncle Ben from Spiderman) once said: “With great power comes great responsibility.”
In other words, if you’re allowing employees to remotely access company devices via RDP, you’re going to have to put a lot more thought into the cyber security measures in place within your organization.
The reason being, RDP is the single most common attack vector used by cyber criminals to gain access to the target system, prior to launching the attack; a fact that’s particularly true for ransomware actors.
Why is it such a popular choice of vehicle?
It’s an Attractive Target
Prior to the ‘big reveal’ (i.e., the moment a successful attacker lets you know that they’ve encrypted all your files and now own your soul), stealth is number one on the cyber criminal’s priority list.
The longer they can remain undetected on the target system, the more they can accomplish – and unfortunately, the worse it’s going to be for you.
RDP provides native access to another device: allowing attackers to ‘live off the land’. In other words, they can utilize anything built into that device’s OS (e.g., PowerShell, Command Prompt, Registry Editor, etc.) to accomplish their goal/s on the target system.
Ease of use also comes into play here. RDP provides the remote user (i.e., the hacker) an exceptionally easy method by which to navigate a computer: a user interface, eliminating the need to work through tools such as PowerShell to perform malicious actions.
It’s for these reasons that RDP is a hacker’s best friend: it provides the ability to remain undercover, move around the remote device with the utmost ease, and establish a very secure foothold from which to launch the attack.
It has Known Security Issues & Vulnerabilities
Although RDP is built-in to the Windows operating system, its default settings are far from safe and are notoriously arduous to configure securely. Several vulnerabilities also exist that allow for its exploitation on unpatched Windows systems – the most severe of these known as ‘BlueKeep’ (CVE-2019-0708).
The wormable (i.e., self-replicating) remote code execution vulnerability allows the attacker to execute arbitrary code on the target system after sending a specially constructed request to Remote Desktop Services (RDS) via RDP – without the need for authentication.
No user interaction is required to exploit this vulnerability; if you’re got unpatched Windows systems with RDP enabled, you’re ripe for the exploiting in the eyes of cyber criminals looking for an easy ride.
It’s Very Accessible
The most prominent reason attributed to RDP’s popularity as an attack vector is how readily available it is.
When enabled, RDP listens by default on TCP port 3389, accepting packets based on its configuration and other security measures in place. An exposed port is one that accepts packets from the internet.
The COVID-19 pandemic saw a huge jump in exposed RDP ports in the first three months of 2020 and the numbers have continued to climb over the past year and half. A simple search on Shodan at around 6pm last night revealed 4,833,6671 exposed default RDP ports, up from 3.5 million in January 2020. By this morning, that number had increased by 31,393.
Yes, you read that right: more than thirty thousand RDP ports we’re opened around the world, listening on TCP port 3389 – exposed to the internet – overnight.
By the time you’ve read this, I’d put money on that number having jumped another few hundred thousand. Heck, at the rate we’re going, it might have cracked the 5 million mark! (Not a feat to be celebrated…).
Leaving your ports exposed to the net can be equated to handing a cyber criminal one of your corporate PCs and inviting them to have a crack at getting into it. Sure, it’s password protected, lockout enabled etc., but the thought of an ill-intentioned hacker being that up close and personal – within a hair’s breadth of your files, network, and servers – is enough to make any executive cringe.
But that’s essentially the same threat posed by RDP: anyone can scan for port 3389, see what IP addresses they hit, and go for it, which explains why it’s such a desirable and widely used attack vector.
It’s Dangerously Cheap
RDP’s accessibility is furthered by dedicated websites that exist solely for the purpose of selling valid RDP credentials – for as little as $3 USD (how’s that for cheap and nasty!). The already easy job of gaining a foothold via RDP becomes even easier, with the steppingstone of brute forcing credentials now removed.
Access & Attack Overview
In order to use RDP as the attack vehicle, bad actors first need to authenticate to establish the remote connection (unless they’ve exploited a pre-authentication CVE, such as BlueKeep). This requires valid credentials.
Gaining credentials is often achieved through brute force, in which hackers try common account usernames with common passwords. Although, with the increasing implementation of account-lockout policies, there’s been a trend towards attackers trying a small number of the most common passwords with a large number of common, or even known, account IDs to circumvent instant lock out from the target device.
Once access is gained, lateral movement is often attempted: the technique in which a cyber criminal moves from the initial foothold device to another, to another, and so on – looking for any account that has administrator rights.
A common tactic enlisted by hackers is the installation of keylogging software so that when an administrator logs in, their credentials can be stolen and used to gain access to the higher-level account.
As with all malware attacks (or at least, the sophisticated ones) privilege escalation is the goal once access is gained, as it gives the attacker the ability to propagate / terminate / exfiltrate / encrypto…nate (you get the idea) unchecked. Attacks initiated through RDP are no different.
Security in Equal Measure
When it comes to RDP, there are two key points to consider:
- The attack vector itself: RDP
- What the attack vector allows.
Let’s look at the first point. There are a number of simple (ish) steps that can be taken to reduce risk and lessen the likelihood of RDP being used as an attack vector in your organization:
- Keep software systems updated to eliminate exploitable vulnerabilities.
- Implement a password policy that enforces the regular changing of long, complex, original passwords.
- Enable Account Lock-out to prevent brute force attacks.
- Use Multi-Factor Authentication (MFA) to combat successful brute force attacks.
- Use a Virtual Private Network (VPN) to avoid RDP exposure to the internet.
- Change the default listening port so that your IP is less likely to be picked up and targeted on the internet.
- Limit Access using a firewall to only allow access from specific IP addresses.
- Don’t use RDP at all. Disable it. Simple as that. (Or not, judging by the climbing number of exposed ports…)
There are various other techniques that could be enlisted in efforts to make RDP more secure but, as mentioned, it’s a burdensome task – and only handles one half of the equation.
As for the other half: what does the attack vector, RDP, allow? What abilities does it provide to the hacker?
The answer to this question is dependent entirely on the level of privileged access the compromised account has: if the account has admin rights, so does the attacker – and their job has just become a whole lot easier.
So, in order to crack down on the abilities an attacker has if they gain access through RDP, you need to secure privileged access – a task made easy through the use of Privileged Access Management (PAM) software.
PAM vs. RDP
PAM software is based on the Principle of Least Privilege (POLP); removing elevated privileges reduces what a user can do on their endpoint and subsequently, what an attacker can do on that endpoint.
It’s important to remember that RDP is just the attack vector: the vehicle used to gain the initial foothold in the target system. Once that foothold is established, an attacker then needs to find the ideal position from which to launch the attack.
PAM software can inhibit the attacker from ever finding that launch position by preventing any activity on the system that requires privileges higher than that of a standard user.
Admin By Request
Admin By Request is a PAM solution that can, in one fell swoop, revoke all administrative privileges and demote accounts to the level of standard user.
Its key features make it ideal for legitimate users:
- Users are still able to perform tasks that require administrative privileges by self-initiating administrator sessions as necessary.
- IT administrators are still able to remotely assist users through the Support Assist feature.
But a nightmare for cyber criminals:
- A legitimate email address, phone number, and reason needs to be provided in order to request and gain elevated privileges.
- An IT administrator must approve the request for elevated privileges before it can be initiated on the endpoint.
- All approved administrator sessions are fully audited and available to IT administrators both during and after the session.
- Alerting controls and malware scanning tools are in place to flag any untoward activity, such as attempts at privilege escalation.
Managing and monitoring elevated access in this way means there is complete accountability: privileged access occurs only upon approval, when absolutely necessary, with a valid reason required – and it’s all logged.
It means that even if a cyber criminal is able to gain that initial foothold through RDP, they’re still no closer to the end goal; there’s only so much living-off-the-land a hacker can do in a system with absolutely no way to escalate privileges without instant detection.
On the other hand, if you’re now convinced to do away with RDP entirely – great! Admin By Request offers an easy solution for that too:
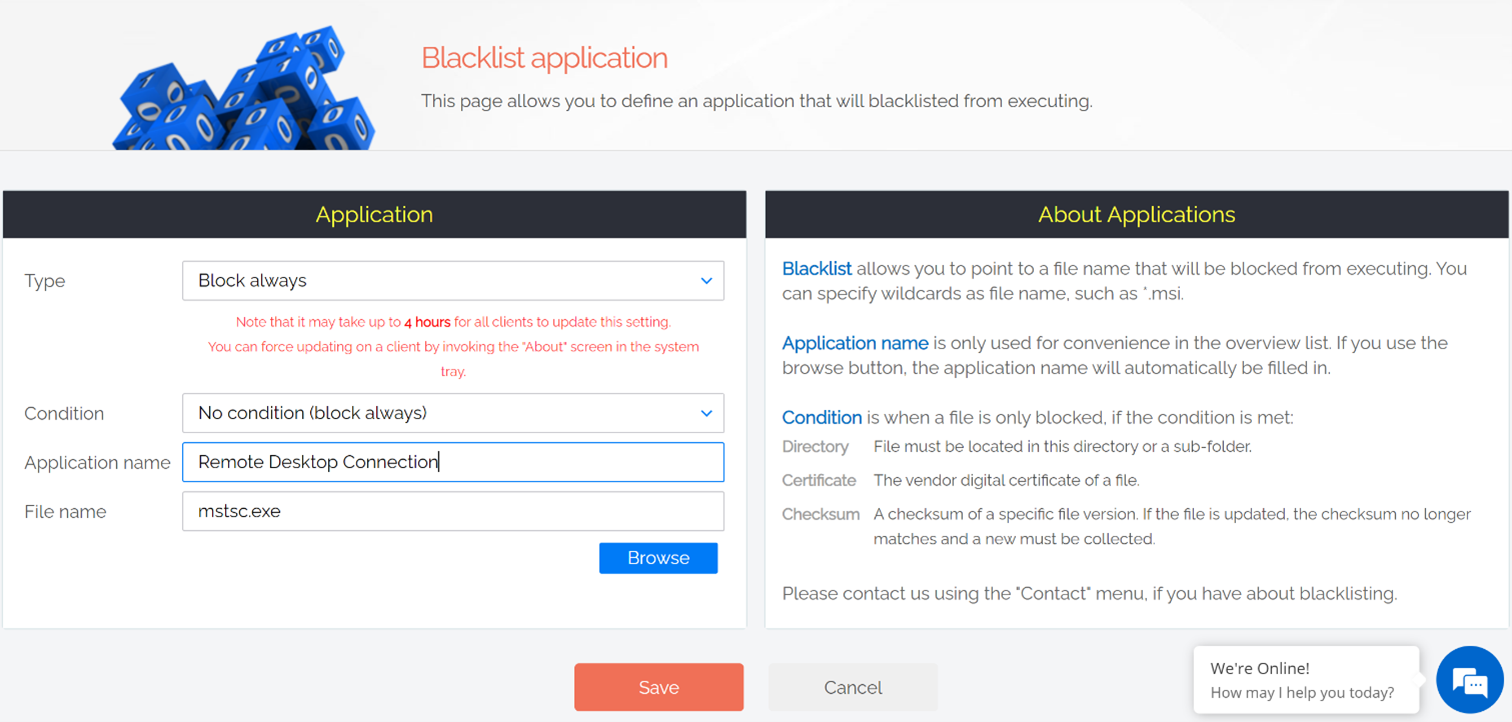
Blacklist the Remote Desktop Connection application, and kiss goodbye to the vulnerabilities that come with RDP.
Conclusion
There are two parts to the RDP attack vector issue: the easy access it provides to cyber criminals, and the abilities they can gain from that access. If you can’t do without RDP in your organization, you need to consider and prepare for both parts of the equation in order to ensure your network is protected.
Try Admin By Request yourself and get those exposed endpoints locked down.






