The Numbers Don’t Quite Add Up
For a long time, Microsoft Windows has won the operating system popularity contest by a fairly wide margin.
According to Statcounter, Bill Gate’s OS is comfortably the top dog with a current market share of almost 75.4% worldwide as of October this year.
MacOS comes in as second favorite, with a share of just under 16%.
You would think, looking at these percentages, that security solutions like ours would be protecting the corresponding numbers of devices running each of these operating systems.
But you’d be wrong.
The actual stats indicate a skewed number of Windows to macOS machines that are covered by Admin By Request‘s endpoint security software, meaning there are more unprotected macOS devices than there are Windows.
So why are Apples struggling to get the protection they need?
The MacOS Malware Myth
It stems from the myth that Apple Macintosh devices “don’t get viruses” – which is exactly that: a myth.
Apple Macs do get infected with malware, but this occurrence has historically occurred to a much lesser degree on macOS than on the Windows operating system.
Here are some explanations behind Mac’s reputation of being immune to malware:
- The sheer number of Windows devices
We know the numbers: there are about four times the number of devices running Microsoft Windows worldwide than there are those running macOS.
1. More numbers mean a larger target. It makes sense for attackers to go for the larger audience: Windows. A larger target audience means more damage can be done; within large companies are thousands of Windows end-user devices, meaning viruses have the potential to propagate further; more money can be made in the case of ransomware when larger, more profitable organizations are targeted.
2. Familiarity with the target OS. Malware isn’t one size fits all: it has to be designed to fit an operating system. Because the Windows platform is more commonly used worldwide, attackers are more likely to be familiar with the Windows operating system and therefore, more skilled in creating malware that is tailored specifically towards this OS.
- Macs are perceived as being harder to crack
Thanks to clever marketing strategies and… a little bit of truth.
1. Apple has always highlighted built-in security as a key feature of the Mac operating system, which, in the early days, may have given some truth to the “Macs don’t get malware” myth. However, with the rise of increasingly complex malware and targeted, hand-launched attacks, built-in OS security alone is not enough to keep up.
2. In classic Apple style, what users and applications can do on the macOS operating system is more restricted compared to the freedom and customization afforded on Windows. For that reason, attacks aimed at Mac devices usually have to rely more heavily on social engineering, making macOS a more difficult target – but still a target, nonetheless.
Can I Order a Big Mac and Files Please?
There is no denying that Mac attacks – once a rare thing – are becoming increasingly common, with high-profile attacks debunking the malwareless-Mac myth once and for all:
2016 – KeRanger Ransomware Trojan
2016 saw ransomware target macOS in the form of OSX.KeRanger, from an infected Transmission (a BitTorrent client) installer. BleepingComputer reported on the infection: executed remotely three days after being installed on the user’s computer, it would then encrypt files and demand payment of 1 bitcoin for decryption. The malicious installer was able to infect 7000 Mac devices, as it was signed with a legitimate Mac certificate, meaning it could bypass Apple’s built-in security – told you so!
2018 / 2019 / 2020 – Trojan-family Shlayer
Under the guise of the Adobe Flash Player installer – a tried and tested favorite – OSX.Shlayer was the biggest threat to macOS users from 2018 to 2019, and has made a return to the macOS scene in 2020. Researchers at Intego did a breakdown on the malware, which, once installed on a Mac device, begins downloading adware and PUPs (potentially unwanted programs) and promoting fake search engines to the user.
2020 – ThiefQuest File-Stealer
In July last year, BleepingComputer analyzed file-stealing and data-destroying malware disguised as ransomware, ThiefQuest. Downloaded from mainstream torrent sites in the form of pirated apps, the packages of compressed installer files appear to be legitimate to the user but contain malicious software and launch scripts, along with legitimate installers. Like most ransomware, files are encrypted upon launch, with no way for victims to contact the attackers after paying the ransom, or for attackers to identify who has paid – prompting the belief that ThiefQuest is stealing data under the guise of ransomware.
2021 – XLoader
For the bargain price of $49 USD, you can now get yourself a Mac MaaS (“Malware-as-a-Service”) tool from the Dark Web, which, according to Computer World, can harvest user logins from browsers, collect screenshots, log key strokes, and download and deploy malware on the victim machine. Named XLoader, the Apple security threat is derived from the data-stealing trojan, Formbook – currently the sixth-most active malware family of all time.
2021 – CVE-2021-30869 in macOS Catalina
In September this year, Erye Hernandez of Google Threat Analysis Group discovered an exploitable vulnerability on Mac’s Catalina OS, allowing malicious applications to execute arbitrary code with kernel privileges and take full control of the system.
Threats like ThiefQuest and XLoader are only going to surge as macOS gains more of a market share while the Windows share decreases; Check Point Software head of research, Yaniv Balmas, agrees: “While there might be a gap between Windows and MacOS malware, the gap is slowly closing over time. The truth is that MacOS malware is becoming bigger and more dangerous.”
Mac Attacks are On the Rise
Malwarebytes Labs confirmed this in their 2020 State of Malware Report: in 2019, for the first time, macOS threats outpaced Window:
.png)
.png)
Figure 1: Graph taken from Malwarebytes Labs 2020 State of Malware Threats Report showing Detections per endpoint 2018-2019.
This was an all-time high for Mac attacks, attributed to the following in the report:
- The failure of Mac security systems to address the huge amount of Adware and PUPs to the same extent that they do malware; a significant problem, as Adware and PUPs made up the majority of the top 10 list of threats to macOS in 2019 in the Malwarebytes Report.
- The user interface. Apple Macs, along with other apple products such as the iPhone, iPad, Apple TV and Apple Watch, are known for their easy-to-use graphical user interface and minimalistic product design. For this reason, it is far more likely for the not-so-tech-savvy staff to work with Apple Macs in the workforce. Users with a lower level of technical skill could potentially appear much more attractive to attackers, who may perceive them as easy targets – particularly when we know Mac attacks rely heavily on social engineering to achieve infection.
And although Mac attacks decreased considerably in 2021 (down 38%), that’s no reason to get complacent; as we know, the trend in market shares shows macOS’s increasing popularity over time, which is undoubtedly going to make it more and more of an appealing target to hackers in the future:
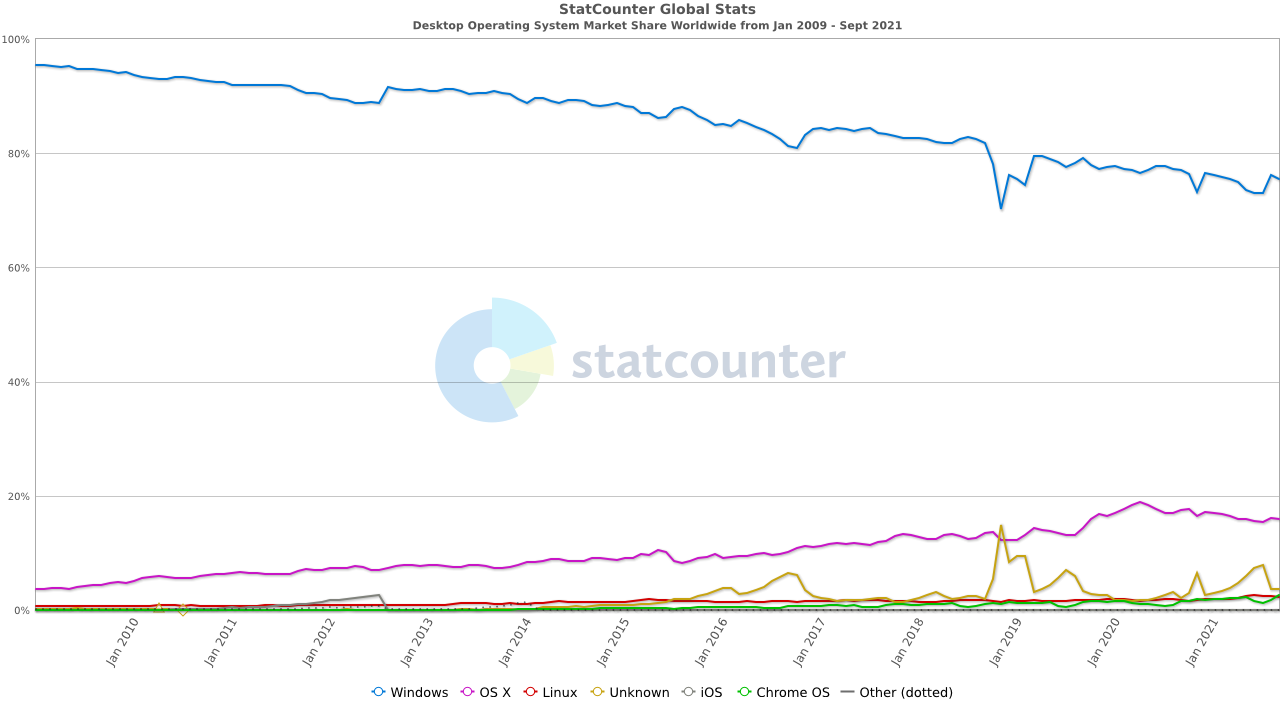
Figure 2: Graph provided by StatCounter showing Desktop Operating System Market Shares Worldwide from 2009 – October 2021.
The maths is simple: a bigger target = more data, damage, and potential financial gains.
Preventing Attacks on Macs: Control, Monitor, Audit
So, what can you do about it?
An all-encompassing solution is to deploy Privileged Access Management (PAM) software on all of your Mac endpoints, to control, monitor, and audit what your Apple users are doing on their devices.
Admin By Request is an endpoint PAM solution that covers the fundamentals:
1. Controls what users have access to.
The solution revokes admin rights so that your end users only have the bare minimum privileges they need in order to do their job. When users do need to do a task that requires elevated privileges, Just-in-Time elevation (JIT) gives them the ability to self-initiate a temporary elevated session – with all file downloads scanned by over 30 anti-malware engines. Controlling user privileges and downloads makes it much harder for users to unknowingly install malware onto the OS – even with the constantly evolving social engineering tactics.
2. Monitors requests for elevated privileges.
The biggest Mac attacks and exploits require privilege escalation to install malware and take control of the OS. With Admin By Request, requests for elevated access – along with user details and a valid reason – are sent in real time to the Admin By Request User Portal, keeping you in the loop of what your users are up to at all times, and why. Elevated privileges can’t be obtained without a request, which in turn can be viewed, approved, or denied, with all data from approved requests logged in the Auditlog – more on this below.
3. Audits elevated activity.
All elevated session data is logged and displayed in the Admin By Request Auditlog, including details of installed or uninstalled software, and programs executed with elevated privileges. This means potential security breaches and attempts to deploy malware and infiltrate the wider network are much more likely to be detected early on and prevented.
Don’t Let your Apples Fall Too Far from the Tree
But the real apple-teaser here is that Admin By Request is a cross-platform PAM solution: it offers a version for macOS as well as Windows, with no AD sync required.
Just to reiterate how sweet of a deal this is, here’s a real-life example:
Scenario: You have an organization with 30,000 Windows devices and a grand total of 7 Apple Macs. You want comprehensive cyber security, and in fact, you’re required to cover ALL endpoints in order to be compliant.
Solution: You can get all of your endpoints – Windows or macOS – fully covered and compliant using Admin By Request as a single, easy-to-deploy PAM solution.
More on that here.
In a Macshell:
So if you’re really serious about taking macOS security seriously – or you simply have a few Apples in your organization that don’t want to be left out – this is your solution to protect all your endpoints before Macs become even more of a target.
Admin By Request offers a free plan for up to 25 endpoints to help you make the move towards a more secure and managed macOS environment – give it a go here and get ahead of the next Mac attack.







